A honeypot is a tool that acts as bait, luring an attacker into revealing themselves by presenting a seemingly tempting target. While advanced honeypots are designed to make it easier to detect and study the kinds of attacks hackers use in the wild, modern honeypots based on tracking URL’s have evolved to be so flexible and user-friendly that average people often use them to identify online scammers.
In our first Security Tools podcast, we explore a free tracking tool called Grabify which can gather information about scammers or attackers when they click on a honeypot tracking link.
Get the Free Pentesting Active
Directory Environments e-book
How a honeypot works
A honeypot is a tool designed to attract an attacker’s attention, allowing a defender to learn more about the attacker’s identity and tactics. While honeypots take many different forms, they’re often disguised as important files, emails, links, credentials, and devices that are most likely to attract an attacker’s attention. An ideal honeypot will appear to be as real as possible, presenting itself as the lowest-hanging fruit in an attempt to blow an attacker’s cover by revealing itself to defenders.
There are a number of creative and useful ways defenders have deployed honeypots to detect and unmask an intruder. The classic “Kippo” Honeypot is famous for pretending to be a vulnerable SSH service exposed to the internet with weak credentials. Kippo lures attackers with the promise of an easy target while secretly recording everything they do inside.
These Honeypots reveal attackers who have breached exposed networks and allows researchers to analyze the payloads automated bots are using to attack vulnerable targets. They also gave rise to a genre of YouTube videos featuring hapless scriptkiddy hackers desperately trying to attack Kippo Honeypots.
To take the deception further, some honeypots even trick hackers into thinking they’ve exited back to their own system while continuing to record everything they do in your terminal window. These honeypots learn more about who the hacker is and what other systems they have access to.
Modern honeypots can be anywhere
Honeypots have evolved to be harder to spot or detect as attackers have caught on and avoid targets that look too good to be true. Using a free CanaryTokin tracker, a defender can embed a tracking link that relies on DNS or web links that run when a PDF file is opened. CarnaryToken collects the IP address of anyone opening the tracked file that might contain privileged information.
To catch attackers gearing up for a phishing campaign, defenders can use honeypot links embedded in website code to identify any time the website is cloned, giving defenders advanced warning if they are targeted.
Other honeypots track stolen credentials by taking the form of fake login credentials called “Honeycredentials,” which are stored in a file with an important-looking name and then left internally for an attacker to easily find. If the attacker tries to use these credentials, the defender is instantly alerted that stolen credentials are being used to try to gain access to an account.
Another application of honeypot tracking links is to know when an attacker is talking about your link in a private online chat like Skype, Slack, or Facebook messenger. This is possible because when you share a link in many chat applications, they often will access the link to generate a helpful URL preview. While the IP address accessing the link belongs to the messenger application and not the attacker, this tactic allows a defender to know if a honeypot tracking link is being shared, even if the attacker is smart enough to never click on the link.
Honeypots can be used by anyone
In the wild west of Craigslist, online dating, and browsing apartment listings, it’s easy to feel like there’s no way of knowing who you’re really talking to. Scammers, catfish, and bots taking advantage of this can be surprisingly convincing, but their stories will often unravel if they can be tricked into revealing information about their location, keyboard layout, or language settings that don’t line up with the story they’re presenting. Because of this, honeypots have caught on among regular people who use web-tracking tracking links to turn the tables on scammers taking advantage of the anonymity the internet has to offer.
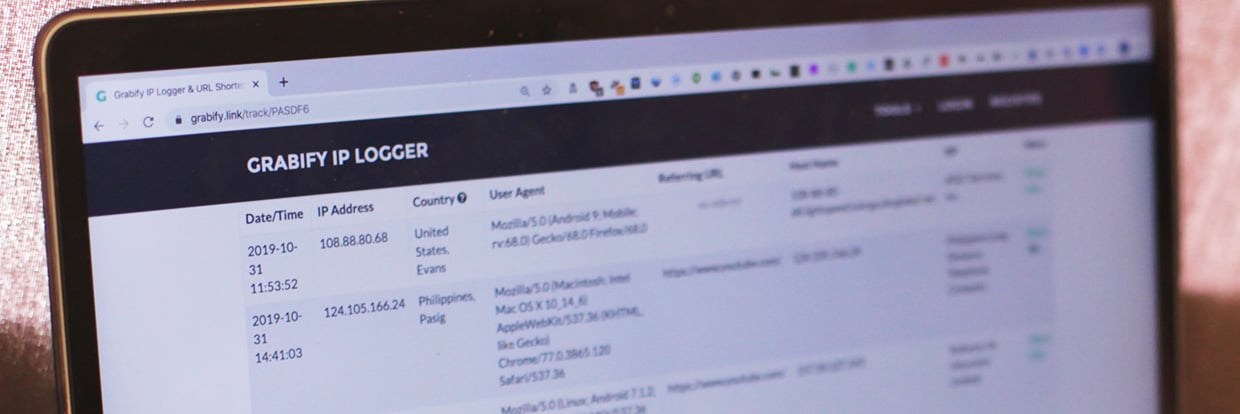
Web-based tracking links are easy to embed inside a webpage, startup script, or email, and are free for anyone to use. If an attacker accesses the link either directly or by opening a file that calls the URL, the defender can begin to profile the attacker’s hardware, software, and network information. Even an attacker attempting to mask their real IP address with a VPN will often leak information about their real identity. Grabify can spot inconsistencies like timezones or keyboard layouts that don’t match the IP location, and even flag when an attacker uses a VPN or Tor to mask their information.
For anyone usually at a disadvantage interacting with suspicious people online, a honeypot tracking link can even the odds by nailing down details which might be otherwise deliberately hard to verify. By using a tracking link redirecting to a website that makes sense to share with a potential landlord, a renter can steer clear of too-good-to-be-true listings by identifying scammers lying about their location. The tracking link would easily uncover someone in India posing as a landlord in Los Angeles online.
Honeypots provide advanced warning
Honeypots are inexpensive and easy to deploy, and one of the best ways to detect when something is wrong. For example, a DNS-trackable CanaryTokin email address within a sensitive contact list can immediately alert you when those credentials are leaked, raising the alarm for something that might otherwise take months to uncover.
Security researcher Kevin Beaumont deployed an RDP honeypot network called “BluePot” to detect BlueKeep exploits in the wild to give advanced warning of a wormable exploit and, hopefully, aid in preventing a widescale attack like NotPeya or WannaCry.
Modern honeypots are pushing the boundaries of how easy to deploy and convincingly deceptive to an attacker they can be. While impressive next-generation honeypots can virtualize entire networks in an attempt to ensnare the more experienced attackers capable of spotting an average honeypot, most companies can benefit even from using simple and free honeypot tactics to be the first to know when an attacker breaks in.
If you want to learn more about the applications and limitations of web-based honeypots, check out our first Security Tools Podcast featuring a discussion with the developer of Grabify!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








-1.png)
