Active Directory Group Policy is a fundamental building block of an enterprise network. Group Policy Objects (GPOs) configure settings, behaviors, and privileges for users and computers connected to the Active Directory domain. Whether you are building a new domain or have an existing domain to manage, you can follow several group policy best practices to have an efficient deployment.
In this article, you will learn about 16 group policy best practices and tips for managing your group policies.
For an introduction on editing Group Policy, check out Jeff Petters’ article Group Policy Editor Guide: Access Options and How to Use.
Get a Free Data Risk Assessment
Tip 1. Minimize change to the Default Policies
Active Directory contains two default policies: the Default Domain Policy and the Default Domain Controllers Policy. The image below displays each policy and where Active Directory links them in relation to the domain.
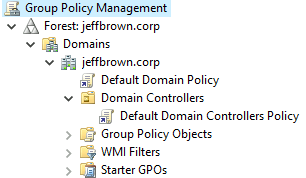
Default Domain Policy
The Default Domain Policy applies settings at the domain level, which affects all users and computers. While it may be tempting to put domain-wide settings here, you should avoid doing so. The Default Domain Policy should only set the following:
- Password Policy
- Domain Account Lockout Policy
- Domain Kerberos Policy
Default Domain Controllers Policy
The Default Domain Controllers Policy applies settings to the domain controllers in the Active Directory environment. The policy is linked to a special Domain Controllers organizational unit (OU). The Domain Controllers OU is a built-in, protected OU where Active Directory places all domain controller computer accounts. The Default Domain Controllers Policy should only set the following configurations:
- User Rights Assignment Policy
- Audit Policy
Tip 2. Minimize GPOs at the root romain level
As mentioned in the previous tip, the Default Domain Policy is located at the root domain level. You should minimize any other GPOs linked at the root domain level as these policies will apply to all users and computers in the domain. If you do need another domain-level policy, create and link a new GPO above the default policy.
Tip 3. Organize your OU structure
A good OU structure makes it easier to manage and troubleshoot multiple group policies. As a general rule, avoid mixing different types of Active Directory objects (like users and computers) in the same OU. Instead, separate users and computers in separate OUs, and you can even organize these OUs by department. Separating out users and computers makes it easier to apply computer policies just to the computers and user policies only to the users.
For example, here is a structure with two different top-level OUs for users and computers. Each structure then contains OUs for specific departments.
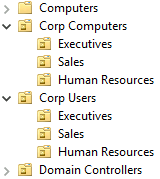
Another method is to have top-level domains dedicated to each department, then create separate OUs for users and computers. Here is an example for the Sales department.

Tip 4. Link GPOs at the OU root level
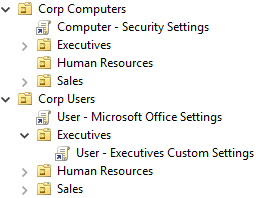
With your OU structure in place, you can start linking GPOs. Link GPOs at the highest level allow child OUs to inherit the settings. This method avoids linking the same GPO to multiple OUs. For example, the image below shows the Computer - Security Settings GPO linked to the root of Corp Computers. This GPO applies to all computers in the organization.
Likewise, the User - Microsoft Office Settings applies to all users in the organization. However, executives require a few custom settings that should not apply to other departments. Therefore, you link the User - Executives Custom Settings GPO to their OU, preventing the settings from applying to other users.
Tip 5. Avoid blocking policy inheritance and policy enforcement
Blocking GPO inheritance at the OU level prevents the application of higher-level policies, such as from a parent OU or the root domain. Policy enforcement ensures that a later policy does not overwrite the GPO settings and configuration.
Using either of these methods can make troubleshooting confusing. You may not be aware that a policy is blocked or a higher policy is being enforced. If a policy is enforced at a higher level but later encounters an inheritance block, the enforced policy will win.
Tip 6. Delete a GPO link instead of disabling
If you want to remove a GPO from an OU, delete the link instead of disabling the GPO. Removing a link does not delete the GPO itself and only ensures the settings are no longer applied. If you disable a GPO, then Active Directory stops using the GPO across the entire domain. This action can cause problems for objects in another OU as the objects are no longer receiving the settings.
Tip 7. Be descriptive with GPO Names
Use descriptive names so you can quickly identify the GPO’s purpose. Looking back at Tip 4, notice the GPO names begin with “User” or “Computer” to indicate the settings configured in the policy. The policy name then shows the policy’s intent, like configuring Microsoft Office or computer security settings.
Tip 8. Disable unused computer and user configurations
Continuing from Tip 7, if a policy only contains computer or user settings, disable the other configuration settings. This action can slightly decrease GPO processing time as the computer or user account does not need to worry about settings that do not apply.
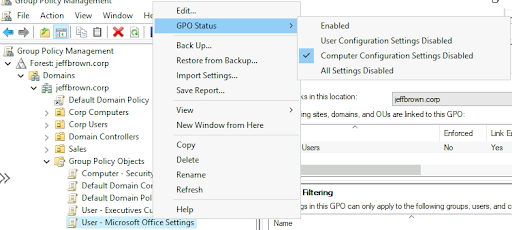
To disable user or computer configuration settings:
- Expand Group Policy Objects in the Group Policy Management console.
- Right-click the policy and navigate to GPO Status.
- Select either User Configuration Settings Disabled or Computer Configuration Settings Disabled. The following screenshot shows computer configuration settings disabled for the User - Microsoft Office Settings GPO.
Tip 9. Simplify administration with smaller GPOs
Avoid cramming every setting and configuration into a single, large GPO. Smaller GPOs enable easier management and simplified design and implementation. As demonstrated in the previous tips, the GPOs target specific settings, such as Microsoft Office or computer security. Some other ideas for smaller policies include:
- Windows Update
- Browser settings
- Network settings
- Bitlocker
- Applocker
- Firewall rules
And many more!
Tip 10. Use WMI filters sparingly
Windows Management Instrumentation (WMI) filters allow you to target GPOs based on computer or user attributes. Attributes in WMI include the operation system version or OS architecture (32 or 64-bit). Using too many WMI filters causes slowdowns at computer startup and user login, which leads to a bad user experience.
Instead of WMI filters, try to use GPO security filters instead. Security filters control which users, groups, or computers that GPO settings apply. By default, any policy is scoped to Authenticated Users, which applies to any authenticated users in the OU.
Tip 11. Backup group policies
Group policies are a vital component of your Active Directory infrastructure and should be treated as such. Therefore, you should perform regular backups of the policies as part of your disaster recovery plans. You can use third-party tools or create a custom PowerShell script using the Backup-GPO command.
Learn more about Active Directory administration and PowerShell in Adam Bertrams’ PownsanerShell and Active Directory Essentials course!
Tip 12. Avoid using the Users or Computers folders in Active Directory
Active Directory comes with default Users and Computers folders at the root domain level. However, these folders are not OUs, and you cannot link GPOs to them. The only way to use GPOs on these folders is to link the GPO at the root domain level, which you should avoid if possible (Tip 2).
Speaking of default folders, there is a default Domain Controllers OU you should keep domain controller computers accounts. Keeping these computer accounts in this OU ensures that domain controller-specific settings are applied consistently to all domain controllers in the environment.
Group Policy FAQ
What is Group Policy?
Group Policy is an Active Directory service that manages configurations for users and computers in the domain.
What is an example of Group Policy?
Examples of group policies include configuring operating system security, adding firewall rules, or managing applications like Microsoft Office or a browser. Group Policies also install software and run startup and login scripts.
Closing
Group Policy is a core service that requires planning and care to ensure an optimal environment. In this article, you learned about 16 tips and best practices when working with Group Policy. While you may not encounter every scenario, understanding the “why” behind certain practices goes a long way in deploying an optimal Active Directory environment.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.