Today's cloud environments offer unparalleled flexibility and scalability, enabling rapid application development, testing, and deployment. However, this flexibility comes with challenges for security teams.
Data is perpetually expanding, managed by various individuals outside of security, making it difficult to defend. As organizations' attack surfaces expand, the associated risks to data, such as overprivileged entitlements and misconfigurations, also increase.
Varonis is excited to announce the expansion of our cloud security coverage to Google Cloud, allowing organizations to automate data discovery, data masking, threat detection, and remediation at scale. Varonis’ coverage now extends across all leading IaaS providers, including Google Cloud, AWS, and Microsoft Azure.
In this blog, we’ll cover the importance of a data-centric approach to cloud security and how Varonis for Google Cloud helps organizations identify and remediate at-risk data.
Cloud security is all about data.
Cloud environments are constantly evolving. With more data in the cloud, and cybercriminals becoming more sophisticated, the risks of data breaches and business disruptions continues to increase. In fact, more than 80 percent of data breaches in 2023 included cloud data.
As the volume of cloud data outpaces security budgets and resources, IT and security teams need security solutions that can be a force multiplier, enabling them to proactively detect and remediate cloud threats. A data-centric approach to cloud security is key to achieving this.
By focusing on the data first, organizations gain a better understanding of their cloud environment, enabling them to build the right controls and implement protection measures early. This approach enhances the overall security posture and ensures that sensitive data remains protected, regardless of where it is stored or processed.
Introducing Varonis for Google Cloud
Varonis provides a unified platform that simplifies and automates cloud security. By taking a data-centric approach to cloud security, Varonis provides unmatched visibility for Google Cloud data and resources, including Google Cloud Storage, BigQuery, managed databases in Google CloudSQL, and unmanaged databases installed on Google Cloud workloads. Varonis identifies where sensitive data lives across Google Cloud, controls exposure, monitors for suspicious activity, and alerts on risks.
View data security risks across your Google Cloud environment by severity in Varonis.
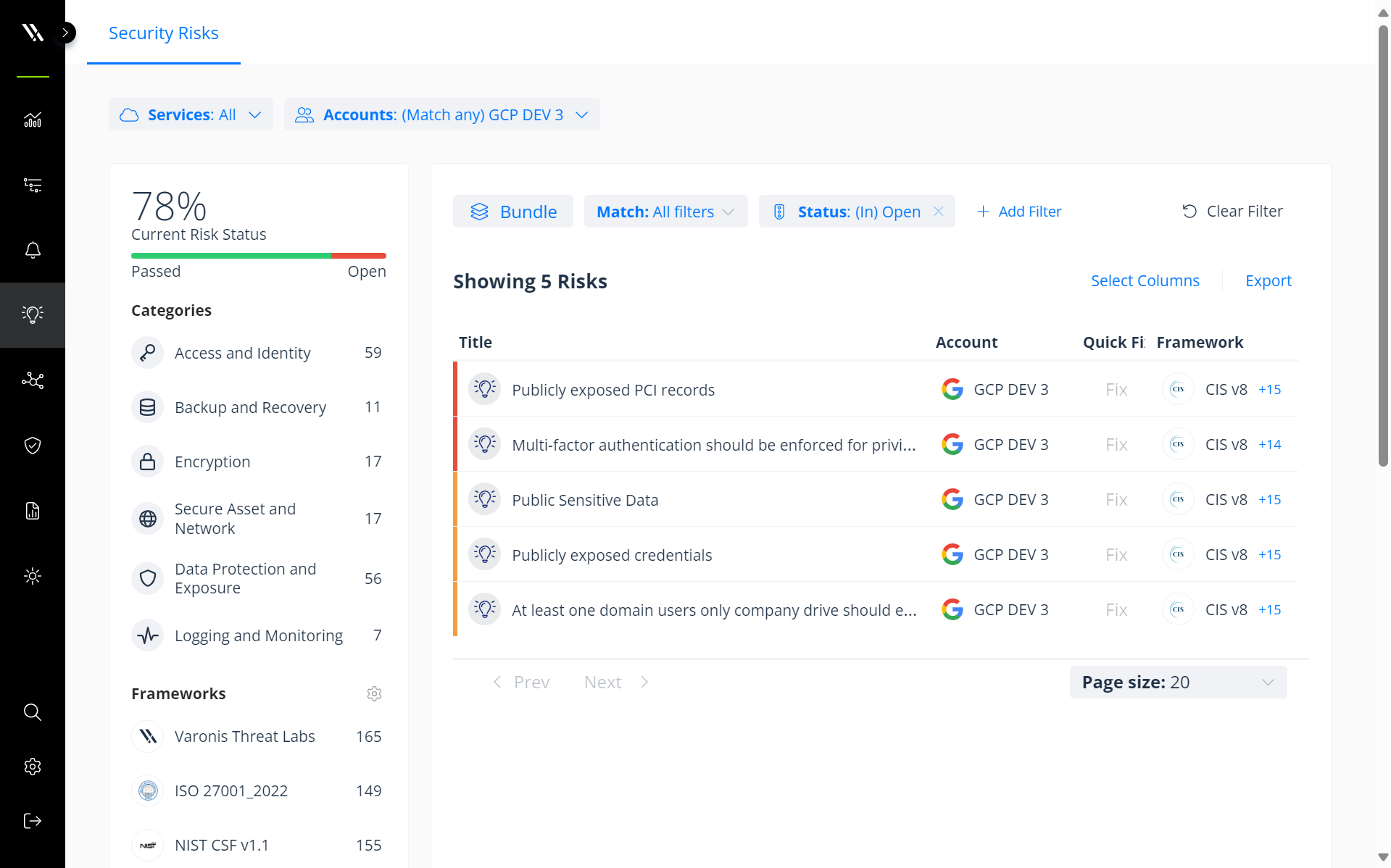
View data security risks across your Google Cloud environment by severity in Varonis.
Identify sensitive data exposure.
Google Cloud environments change fast, and security teams need to keep pace with a real-time understanding of data risks. Varonis is built for petabyte-scale Google Cloud environments and automatically discovers and classifies sensitive data with pinpoint accuracy, identifying where data lives, is exposed, or is at risk.
Varonis also monitors data activity in real time, giving you complete, searchable, human-readable audit trail of events in Google Cloud.
Automatically mask sensitive data.
Once sensitive data is identified, it’s critical to control who can view it to reduce the risk of breaches. Varonis for Google Cloud automatically protects sensitive data like PII, PCI, and PHI in BigQuery based on users’ roles with dynamic data masking capabilities.
Varonis’ data masking can provide either masked or original data in real-time, depending on the user or role requesting the data, reducing the risk of sensitive data being overexposed.
Detect sophisticated threats.
When securing data in the cloud, threat detection is vital to identifying active intrusions, such as stealthy attacks and insider attacks. Varonis uses predictive, behavior-based threat models to automatically detect abnormal activity in Google Cloud and alert you to potential threats before they become breaches.
Using machine learning to build baselines for every unique user and device in your environment, hundreds of expert-built threat models alert you to unusual access activity, permissions changes, data transfers, and more.
Accelerate investigations and remediation.
Once an organization identifies risks to their data, they must quickly fix issues and close vulnerabilities before they are exploited. Varonis automatically performs investigations, responding to threats and closing alerts without requiring human intervention.
Varonis data security experts also ensure your business is protected from breaches with our Managed Data Detection and Response service that provides 24x7x365 incident response, alert monitoring, and security posture management.
Try Varonis for Google Cloud at no cost.
Varonis for Google Cloud offers security teams a single control point to discover, monitor, and protect structured and unstructured data across Google Cloud.
Ready to improve your cloud and data security posture and secure your most sensitive Google Cloud data? Request a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.
.jpg)