Endpoints – the laptops, smartphones, and other devices we use on a daily basis – are a favorite target of attackers. They’re everywhere, prone to security vulnerabilities, and difficult to defend. 2017’s WannaCry attack, for example, is reported to have affected more than 230,000 endpoints across the globe. Endpoint Detection and Response (EDR) is a fast-growing category of solutions that aim to provide deeper capabilities than traditional anti-virus and anti-malware solutions. In this piece, we’ll learn what EDR is and why it’s important, discover how EDR security solutions operate and examine some best practices for using these tools.
- What is Endpoint Detection and Response (EDR)?
- Why is EDR Important?
- How Does EDR Work?
- 9 Elements of EDR Solutions
- Benefits of EDR Security
- Endpoint Detection and Response (EDR) vs Anti-Virus vs Endpoint Protection Platform (EPP)
- EDR Security Tips and Best Practices
Get a Free Data Risk Assessment
What is Endpoint Detection and Response (EDR)?

Endpoint detection and response (EDR) is a category of solutions that can detect and respond to suspicious activity on an organization’s desktops, laptops, and mobile devices. The term was coined by Gartner analyst Anton Chuvakin in 2013 to describe emerging platforms that allowed for a deep level of investigation into suspicious activities. EDR is also distinct from other security solutions like firewalls in that it applies protection directly on the computers on the network, and not at the network boundary.
Why is EDR Important?
From Advanced Persistent Threats (APTs) to fileless malware, organizations today face a range of cyber-threats that legacy security products simply miss. Attackers have become highly adept at outmaneuvering signature-based protections like anti-virus software and Intrusion Detection Systems (IDS). Every device that connects to a network is a potential attack vector for cyberthreats, and the rising popularity of mobile devices and remote work erodes the effectiveness of perimeter-based defenses like firewalls.
EDR security solutions couple large amounts of data captured from each endpoint with contextual analysis to detect elusive threats that may never have been seen before. Most EDR solutions use baselining and behavioral analysis to spot potentially suspicious activity, and many can even respond to events in real-time.
In contrast to other solutions, endpoint detection and response is often most valuable during and after a breach. The highly detailed information available in EDR platforms allow security teams to uncover how a threat evaded existing defenses. Realtime alerts from the EDR solution can help an organization spot the early stages of an attack, and take action to prevent a full-blown data breach. If a breach does occur, the capabilities offered by such platforms greatly aid investigation and remediation efforts.
How Does EDR Work?
Endpoint Detection and Response is often compared to the flight data recorder or “black box” found on commercial aircraft, and for good reason. Just as a black box continually collects telemetry from an airplane’s flight systems, EDR platforms are constantly ingesting data from endpoints in the form of event logs, authentication attempts, running applications, and more. The details may vary between different vendors, but in general EDR security solutions operate as follows:
-
Telemetry is Ingested from Endpoints
A wide range of telemetry data is gathered from the endpoints. Typically, this is done through the use of a software agent installed on each endpoint, but in some cases, the telemetry may be collected through indirect means.
-
Ingested Telemetry is sent to the Larger EDR platform
Data from each of the endpoint agents are sent to a central location, often a cloud-based platform provided by the EDR vendor. Industries with special compliance requirements may use an on-premises or hybrid cloud implementation.
-
Data is Correlated and Analyzed
Algorithms and machine learning technology sift through the vast amounts of data collected and highlight potential irregularities. Many EDR solutions will “learn” what normal user behavior and endpoint operations look like. Data can also be correlated across multiple sources, including other security products. Threat intelligence feeds are often used to provide real-world examples of ongoing cyberattacks that can be compared to activity within an organization.
-
Suspicious Activity is Flagged and Responded To
Any events or activity that the EDR platform views as suspicious generates an alert for security analysts to review. The automation capabilities present in many EDR security solutions can also take direct action in response to a threat. For example, the solution may temporarily isolate an endpoint from the rest of the network to prevent malware from spreading. More significant threats may require a high degree of human intervention.
-
Data is Retained for Future Use
Data retention is an important feature of endpoint detection and response. As new types of cyberattacks are discovered, security teams can dig through older data to see if they may have been the victim of a previously unknown attack. Archival data can also be used for proactive threat hunting – essentially probing large volumes of data with the preconceived expectation of malicious activity.
9 Elements of EDR Solutions
Endpoint detection and response solutions can have a range of features – but there are a set of core elements that are essential to EDR:
- Console Alerting and Reporting: A role-based console that provides visibility into the organization’s endpoint security status
- EDR Advanced Response: Advanced analysis and response capabilities of EDR solutions, including automation and detailed forensics about security incidents
- EDR Core Functionality: The capability to detect and report on security threats and vulnerabilities on the endpoint
- EPP Suite: Basic functionality that was available in the previous generation of endpoint security software including anti-malware, anti-phishing, and anti-exploit capabilities
- Geographic Support: An EDR vendor’s capability to support a global enterprise – because information security is mission-critical
- Managed Services: The EDR’s ability to feed data to a Managed Security Service or Managed Detection and Response vendor to further augment the security team’s capabilities
- OS Support: In order to be effective, an EDR needs to support all of the operating systems in use by your organization,
- Prevention: It’s not enough to simply detect a threat – effective EDRs need to provide preventative measures as well, to help mitigate and enable teams to take action.
- Third-Party Integration: A comprehensive data security strategy often requires integrating with multiple products: EDRs should have APIs or built-in integrations with other solutions to complement and deliver on a layered security approach.
Benefits of EDR Security
EDR can provide a wide range of benefits when used correctly. These may include:
-
Deep and Wide Visibility
Visibility is a core component of all EDR solutions, and that visibility is both deep and wide. Deep visibility comes in the form of being able to dig into the inner-workings of the endpoint and inspect the relationships between processes, network connections, and user behavior. At the same time, the centralized nature of EDR means that analysts get a wide view of the organization’s security posture, and can spot patterns across dozens, hundreds, or even thousands of endpoints.
-
Detection of Advanced Threats
One of the key benefits promised by EDR is the ability to detect threats that may otherwise have gone unnoticed. These may include zero-day attacks, insider threats, highly sophisticated hacking campaigns, and more.
-
Simplified Incident Response
The rich level of detail collected by EDR solutions can greatly simplify response and remediation activities following a breach. In the past, an incident responder would spend a great deal of time collecting artifacts from various endpoints to create a larger pool of evidence. EDR collects and stores these artifacts as part of its normal operation. Centralized EDR consoles and longer data retention periods can also provide a more complete picture of a security incident than would otherwise be available.
-
Automation and Integration
EDR products frequently include robust automation capabilities, and custom integration is often possible through the use of an API. Since EDR agents are usually installed on all endpoints across an organization, investigation or response activities can be rapidly initiated at scale.
Endpoint Detection and Response (EDR) vs Anti-virus vs Endpoint Protection Platform (EPP)
In principle, EDR is about detecting and responding to threats that have evaded other layers of defense. In practice, however, many vendors combine EDR functionality with other types of security capabilities. Most EDR products offer the same sort of signature-based malware protection that legacy Anti-Virus provides. Endpoint Protection Platform (EPP) is a term that is frequently used to describe products that combine EDR, Next-Generation Anti-virus (NGAV), and other types of protection in a single piece of software. Additional capabilities offered in EPP products may include host-based firewalls, control over device encryption, data loss prevention, and more.
EDR Security Tips and Best Practices

EDR can be a powerful addition to an organization’s overall information security program but requires thoughtful implementation. To get the most out of an EDR investment, an organization should:
-
Be Aware that EDR Solutions Require Human Talent
In a large organization, EDR security solutions may generate tens of thousands of alerts each day. Many of these alerts may end up being false positives. To realize the true benefits of EDR, organizations must invest in human security analysts who can make sense of the computer-generated data. This is often an expensive investment, as a skilled security analyst can command a relatively high salary. Smaller organizations might look to Managed Detection and Response (MDR), an as-a-service offering that marries EDR with human analysis.
-
Choose a Vendor Based on Your Organization’s Specific Requirements
The capabilities – and cost – of an endpoint detection and response product can vary tremendously. Organizations should spend a good deal of time researching the products from multiple vendors to ensure a good fit. For example, does the vendor offer an EDR solution that works well with the operating systems and applications already in use? And how does the solution integrate with other security tools? Failing to ask these kinds of questions can end up in a bad fit that negates the benefits of endpoint detection and response.
-
Use it as an Adjunct, not a Replacement
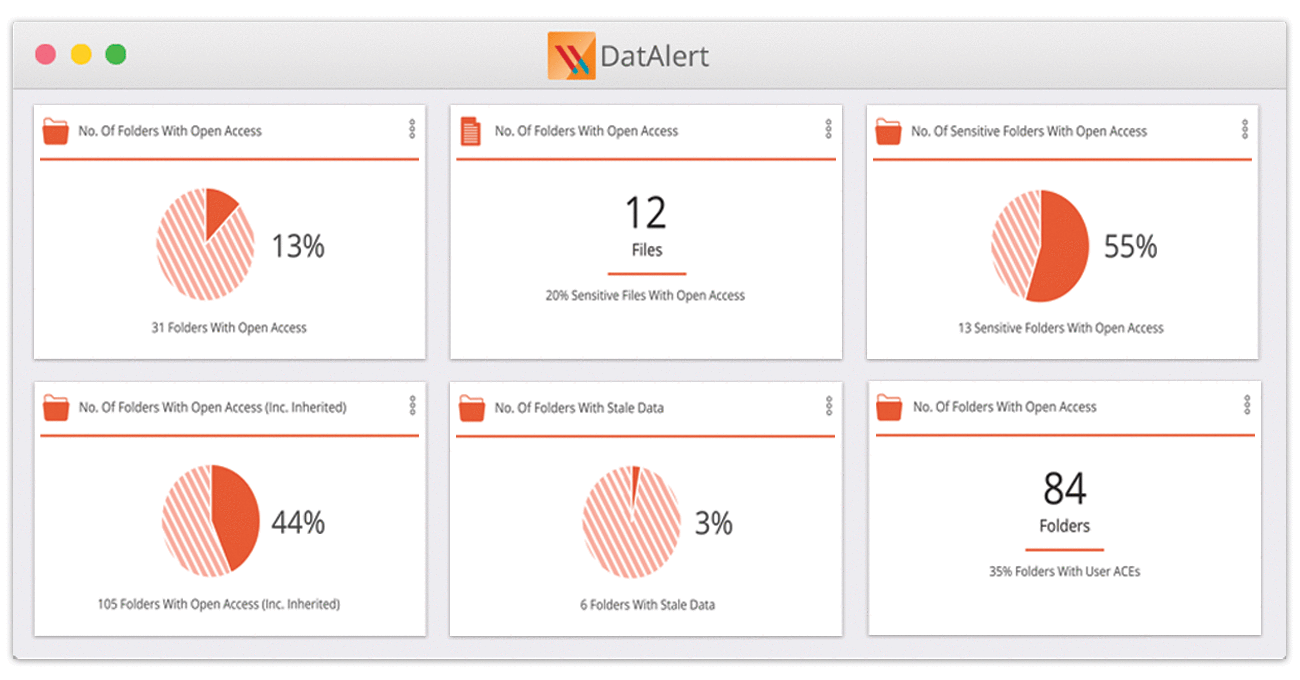
Endpoint Detection and Response is called such for a reason; its focus is solely on endpoints. Some behaviors that might look normal on an endpoint – a user logging in with a valid user and password, for example – wouldn’t necessarily raise a red flag with an EDR alone. However, that login event might be suspicious if it logs in from multiple locations within a short time. Varonis DatAlert and Edge analyze file activity, user events, and perimeter telemetry to identify abnormal behavior with added context: so that even seemingly harmless activity is considered in context to get the bigger picture.
While an EDR solution protects the endpoints on your network, they’re limited in what type of activity they can monitor and limited in what type of malware or cyberattacks they can detect. Varonis is designed to protect enterprise data from zero-day attacks beyond the endpoint – putting perimeter telemetry in context with file activity and user behavior from your core data stores.
See how EDR and Varonis can work together – click here for a 1:1 demo and see how a layered security strategy works in your environment.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.