All industries rely on data, and this data is increasingly stored in dynamic cloud environments. For organizations handling sensitive data in the cloud, data security posture management (DSPM) is essential for ensuring security and compliance.
Most enterprises use multiple clouds with large, sometimes outsourced, development teams, constantly spinning up new resources. With databases, object storage, SaaS applications — and now AI training pipelines — there is too much data in disparate data sources and too many attack vectors to secure by traditional means.
With the big three cloud providers — AWS, Microsoft, and Google — providing excellent APIs, developing DSPM capabilities became easier than developing data security capabilities for traditional on-premises environments. DSPM capabilities quickly advanced, and now, DSPM is vital for securing data in dynamic cloud environments.
In this blog, we’ll discuss the key use cases for DSPM and explain why this framework is only one part of a holistic approach to data security.
DSPM use cases
DSPM helps address three of the biggest challenges to securing cloud data:
Where is my sensitive data?
In cloud environments where data can be created, cloned, and moved easily, the first step to securing data is understanding where it resides. DSPM automatically scans and discovers sensitive data across your environment and classifies it based on its sensitivity and type, such as whether it is credentials, PHI, PII, HIPAA data, etc.
Is my data at risk?
Identifying the location of your sensitive data is just the beginning. Next, you must determine where it is exposed and at risk.
Is there an unsecured bucket with PII in it? Is there high-risk access to confidential HR data? Is someone using stolen credentials to move laterally across our environment?
To understand risks and exposures, you need DSPM capabilities that map sensitive data to permissions and access activity across platforms, applications, and all the way down to the object level. Without this deep understanding, your security posture can be easily compromised.
How do I make my data more secure?
Finally, you need to fix the issues that put your data at risk — and fast. The longer it takes to fix issues (e.g., eliminating risky permissions, fixing misconfigurations, removing global sharing links, etc.), the greater the risk of a data breach.
The number of issues and misconfigurations in the cloud that need to be addressed quickly add up and outpace the ability of IT and security teams to remediate them manually. To address this, DSPM capabilities should include automated remediation, enabling an environment that becomes more secure over time.
Any organization with sensitive data in the cloud should consider DSPM a core part of its approach to data security. That said, there are cases when DSPM is considered exceptionally useful.
Business cases for DSPM
Let’s take a look at a few examples of different business cases that warrant a need for DSPM.
Mergers and acquisitions (M&A)
M&A presents unique challenges for security teams. Now they are responsible for securing data from both companies spread across even more clouds, applications, and databases. M&A may also mean that you are subject to different data residency and regulatory requirements, like HIPAA, GDPR, CCPA, NIST, ITAR, or the new EU AI Act.
Essentially, a merger or acquisition takes the challenge of securing data in the cloud and doubles it. In these cases, DSPM is critical for identifying sensitive data across both companies, identifying and remediating risks before they can be exploited, and providing a holistic picture of regulatory requirements.
Data privacy audit
When trying to comply with certain regulations, like GDPR or CCPA, it’s common for orgs to perform a comprehensive review process to assess its handling of personal information.
DSPM can help identify data related to these regulations and assess risks. Varonis goes further and creates a normalized record of every action on your data — in the cloud and on-prem. This provides you with a complete history of files, folders, sites, permissions, mailboxes, and more. This audit trail of activity makes conducting a thorough data privacy audit much easier.
Cloud migration
Whether you are moving from on-prem to the cloud or migrating from one cloud environment to another, cloud migration is a big undertaking. From a data security perspective, it’s challenging to understand what sensitive data is being moved.
The cloud also comes with numerous potential attack vectors that don’t exist on-prem and are created during migration. For example, the transition can easily expose a database snapshot or S3 bucket to the internet, and attackers can exploit high-risk permissions.
DSPM enables you to track all your sensitive data as it moves from one environment to the next. DSPM can also be instrumental in detecting exposure and risks created during the migration process.
DSPM: The tip of the iceberg
DSPM is one part of a holistic approach to data security.
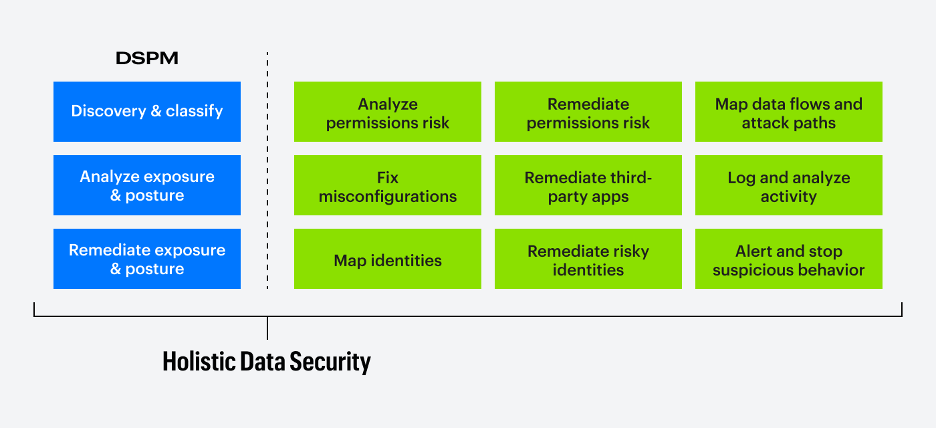
DSPM is one part of a holistic approach to data security.
While essential for cloud data security, DSPM is only one part of a holistic data security approach. Other capabilities are just as important, including:
Data access governance
Data access governance is critical for approving and denying access to data and right-sizing permissions, eliminating unnecessary exposure and complying with regulations.
Data loss prevention
Data loss prevention (DLP) protects information from theft or loss that could result in fines or decreased productivity. DLP can be essential for securing data and enforcing policies.
Data-centric threat detection
Even in secure environments, sophisticated attackers will still find a way in. Data-centric threat detection is necessary for detecting active threats, particularly hard-to-detect techniques like insider attacks and breaches that stem from stolen credentials.
User entity behavioral analytics (UEBA) is also important for building threat models and identifying atypical behavior that can indicate an attack.
Do more with DSPM
Ready to improve your security posture automatically? Book a demo with our team to learn more about Varonis' unique DSPM capabilities.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.