The growing list of high-profile data breaches demonstrates that traditional perimeter-focused security can’t address the data security challenges we face in a cloud-first era. Minimal data lives on endpoints, which serve primarily as gateways to where critical data really lives: in complex hybrid cloud environments.
Most enterprises use dozens of collaboration apps like Microsoft 365, Google Workspace, and Salesforce — all of which house mission-critical data. Add hybrid NAS devices, on-prem file shares, AWS, Azure, and GCP, and it’s easy to see why enterprises have lost visibility into where their sensitive data lives, who has access, and whether it’s under attack.
Enter Data Security Posture Management (DSPM)
Data security posture management (DSPM) provides visibility as to where sensitive data is, who has access to that data, how it has been used, and what the security posture of the data stored or application is.
Gartner
Although DSPM is a new acronym, data discovery, data access control, and data monitoring are not new concepts. The emergence of DSPM as a product category has helped bring much-deserved attention to data security at a time when data sprawl, complexity, and risk are at an all-time high.
We designed this guide to help you understand the different types of DSPM solutions available on the market today, avoid common pitfalls, and ask questions to ensure you purchase a data security solution that meets your unique requirements.
Three evaluation tips from CISOs
1. Run a proof-of-concept (POC).
'My golden rule when evaluating any new technology is to validate claims with a POC. Vendors who refuse to do a POC should raise red flags. Try to do POCs on production systems or sandboxes that mimic your production environment’s scale. For DSPM, test data classification results for false positives.”
2. Ask for a sample risk assessment.
“Ask to see an anonymized risk report from a real customer — not a marketing brochure. This can help you understand if the vendor offers the level of granularity and depth you’re after. Sample reports can help you determine if a POC is worthwhile.”
3. Read real customer reviews.
“Be careful judging vendors based on awards and press, many of which are pay-to-play. Look for validated DSPM reviews from trusted sources like Gartner and Forrester. Ask to speak directly to reference customers. Make sure they have customer case studies on their website. You don’t want to be their first big customer.”
Not all DSPM solutions are created equal
Many vendors are trying to ride the DSPM wave. The market is full of solutions advertised as DSPMs that don’t actually improve your data security posture or help stop data breaches.
Here are a few passive DSPM-like solutions to look out for.
Discovery-only DSPM
Vendors with roots in data privacy and governance are masquerading as DSPMs. They lack the context needed to identify whether sensitive data is at risk, resulting in non-actionable information. These products measure data security posture by counting sensitive data findings and do not consider exposure levels, fix issues, or detect threats to data. Discovery-only DSPMs are essentially data catalogs.
IaaS-only DSPM
Many DSPM vendors focus on the big three IaaS platforms (AWS, Azure, and GCP) and ignore other critical data domains like cloud file storage, on-prem file shares, SaaS apps, and email. While databases and buckets in multi-cloud environments are crucial to secure, look for a DSPM vendor that spans all your data domains so you can have unified visibility and apply consistent policies across the board.
DSPM vendors without cybersecurity expertise
Just as you’d expect your EDR/XDR vendor to have strong threat intelligence and research capabilities, your data security vendors should have research teams focused on finding vulnerabilities, tracking threat actors, and developing new threat models.
Top five things to look for in a DSPM
1. Coverage across all data domains and data types
Most large organizations store critical data in three big domains: File, SaaS, and IaaS.

Buying a DSPM that only covers a single domain would be like purchasing an EDR that only worked for Macs.
It might be impossible to find a single DSPM that covers every single data store your business uses. Instead, follow the 80/20 rule. Ask yourself where your most mission-critical data lives and prioritize those data stores.
2. Accurate and scalable data classification
Data discovery and classification are a foundational element of DSPM. Many classification projects fail because the scanning engine can’t process large data sets or they produce too many false positives to be trusted.
Look for a DSPM with customers that match your size and scale. During your POC, ensure their classification can produce complete, contextual, and current results.
- Is your data classification complete?
Does your DSPM scan all your data, or is it over-reliant on sampling or “predictive” scanning?
Sampling can be effective for databases but doesn’t work for large file stores like NAS arrays or object stores like S3 and Azure Blob. Unlike a database, you can’t assume that just because you scanned 2TB of an S3 account and found no sensitive content, the other 500TB of data is not sensitive. - Does your data classification have context?
Once you find sensitive data, what happens next? Is the data exposed?
Is it being used? Who is the data owner?
Most organizations are surprised at the number of sensitive files and records they find — and the list will be different tomorrow and the next day. If your DSPM does not map permissions or track access activity, it’s virtually impossible to action the finding. - Is your data classification current?
Does your DSPM scan and classify data as it is created and modified?
If your DSPM does not keep a real-time audit trail of data activity, its classification engine must check the last modified date on every single object to know whether it must be re-scanned or perform a full re-scan at specific intervals (usually monthly or quarterly).
3. Deep analysis beyond data classification
What does it mean to truly “cover” a platform?
Many DSPM vendors will check the coverage box for any platform they can connect to, regardless of whether they provide actual DSPM capabilities. Some vendors will even purport to cover a data store, but in reality, they simply provide you with a developer SDK, and you have to build your own connector.
DSPM must go beyond answering whether a file or object is sensitive, taking into account whether data is at risk of a breach, and answering questions like:
- Is our data being used, and by whom? Are there any abnormal access patterns that could indicate compromise?
- Is our sensitive data labeled correctly so that our downstream DLP controls work?
- Is sensitive data exposed publicly, to all employees, or to people who don’t require access?
- Is our sensitive data stored in unsanctioned repositories? Are we in violation of any data residency requirements?
- What is the likelihood that a compromised user could exfiltrate sensitive data?
- What data is stale and can be archived or deleted?
Here's a helpful scorecard of eight critical DSPM ingredients and two bonus questions you can provide vendors to better understand the depth of their coverage for each platform:
Ask these questions when evaluating a DSPM solution for your org.
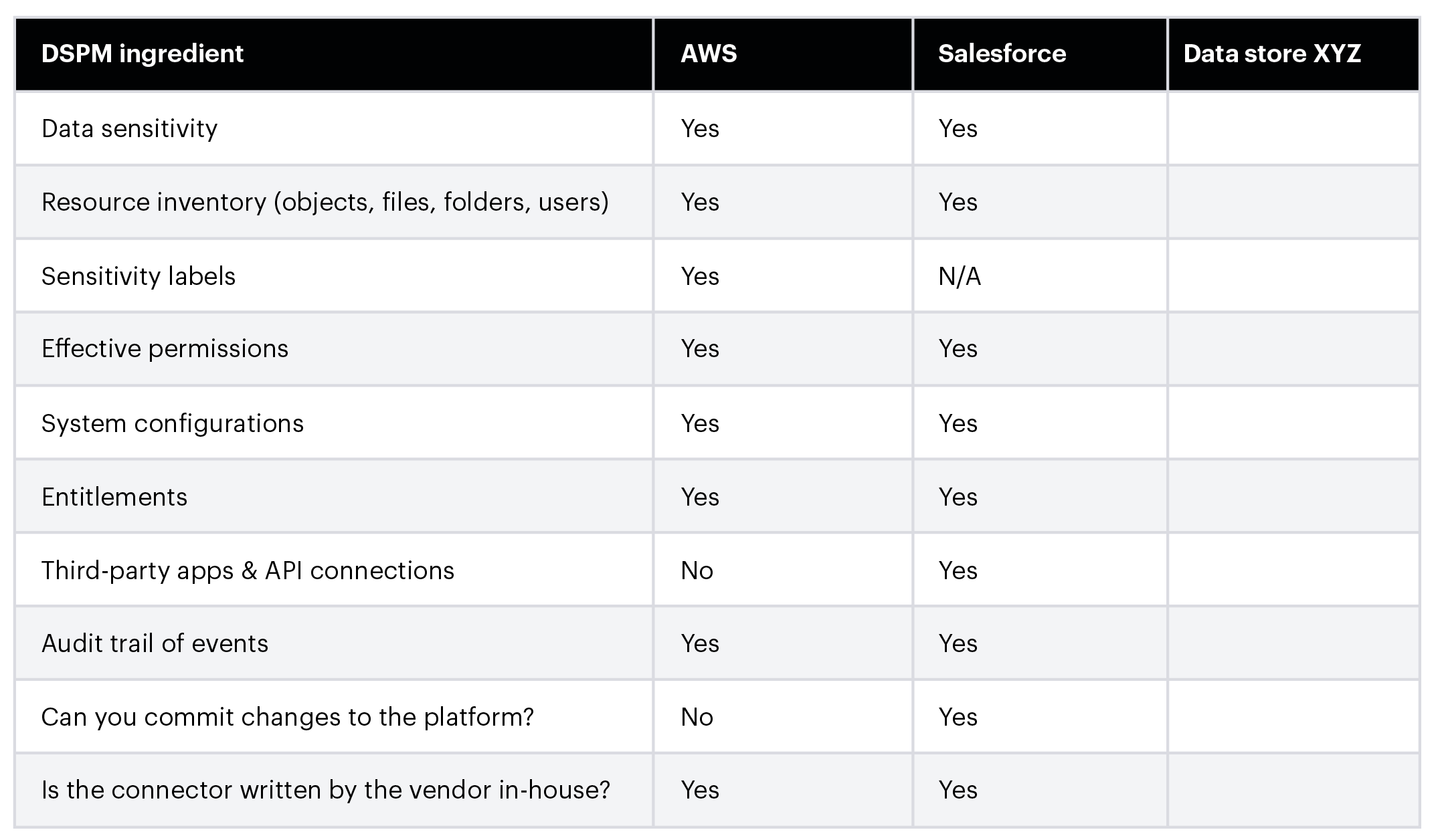
Ask these questions when evaluating a DSPM solution for your org.
Entitlements vs. effective permissions
One of the most critical data security questions is: who can access sensitive data?
This question is not always easy to answer. In fact, calculating true effective permissions for a user in real-time can be computationally challenging and goes far beyond simply reporting on a user’s entitlements. This task is difficult for platforms like Microsoft 365 and Salesforce, which have complex permissions models.
Entitlements are permissions or rights assigned to a user, group, or entity.
Effective permissions represent a user or entity's permissions for a resource. They take into account the cumulative effect of all entitlements and access control settings, including inheritance, muting permissions, group memberships, explicit grants, global access, and other dynamic factors.
Your DSPM’s ability to visualize effective permissions is absolutely critical for breach investigations, compliance audits, and other data security use cases. This visualization is impossible without building specialized connectors for each data store and application.
4. Automated remediation
CISOs don’t need another product to tell them they have problems without offering an automated way to fix them. Look for a DSPM solution that goes beyond visibility and automates fixes on the data platforms it's monitoring.
When a vendor says they offer automated remediation, ask:
- Do you commit changes to the target platform to remediate the risk?
- Can you simulate the change before committing?
- What are the specific data risks that you can remediate automatically?
- Can you automate remediation natively, or does it require clicking a button or executing a homegrown script?
Often, vendors will claim automated remediation when they simply open a ServiceNow ticket (often called a “finding” or a “case”) for a human data owner to investigate, fix, and close manually.
5. Real-time behavioral alerts and incident response
Data is the target of almost every cyberattack and insider threat.
Finding sensitive data and ensuring that only the right people have access are essential to maintaining a strong data security posture. However, DSPM must also be able to monitor data access, alert you to abnormal behavior, and stop threats in real time.
As we mentioned earlier, it’s a red flag if your DSPM vendor does not have an incident response function and a cybersecurity research team that regularly publishes data-centric threat research.
Look for a DSPM vendor that incorporates data detection and response (DDR) and can achieve the following:
- Log all actions on data, not just alerts.
- During an investigation, you want a full searchable forensics audit trail inside your DSPM. You don’t want to have to jump into your SIEM or come up empty when asked to see all actions on a specific data set.
- Alert you to behavior anomalies.
- If your DSPM only has static rule-based alerts (e.g., alert when a user modifies more than 100 files in under a minute), you run the risk of missing stealthy attacks and insider threats. Find a DSPM with data-centric user and entity behavior analysis (UEBA) capabilities.
- Help you respond to incidents.
- Does your DSPM vendor have a team that can help you investigate an incident? At a minimum, can their alerts be sent to your SIEM, SOC, or SOAR so that your own incident response team can respond to threats to sensitive data?
How Varonis delivers on DSPM
Varonis is purpose-built to secure enterprise data—wherever it lives. Varonis offers deep, unified coverage across structured, unstructured, and semi-structured data. Beyond just identifying risk, Varonis continuously reduces it through automation, deep context, and real-time response.
Full-stack data protection
Varonis covers structured, unstructured, and semi-structured data across all three DSPM domains: data classification, access intelligence, and risk mitigation. The platform protects sensitive data across hybrid environments and understands the attack paths that lead to it: from Active Directory and Entra ID to VPNs, proxies, and API/OAuth connections.
Context-aware data classification
Varonis provides complete, enterprise-scale data discovery and classification. We scan massive, multi-petabyte environments and contextualize sensitivity with real-time activity and access rights. Our classification remains accurate and current thanks to continuous auditing—eliminating the need for costly rescans or reliance on static file metadata.

Varonis data classification
Visibility for better decision-making
With more than 150 patents, Varonis combines rich metadata from eight key sources to answer the most critical data security questions:
- Where is our sensitive data?
- Who has access to it?
- Is it at risk, exposed, or stale?
This depth of insight also powers our ability to automate at scale—revoking unused or risky permissions with confidence that business continuity won’t be disrupted.
Automated remediation, built-in
Varonis continuously remediates risky access, misconfigurations, ghost users, and public or overshared links with out-of-the-box policies that can be tailored to your needs. No manual effort required.

Customize ready-made policies to enable remediation actions automatically in Varonis.
Real-time threat detection with data-centric UEBA
Varonis gives security teams a complete audit trail of all data activity—across cloud and on-prem environments. Hundreds of expert-built threat models detect abnormal behavior like unusual access patterns, geo-hopping, and suspicious permission changes. Plus, with Managed Data Detection and Response (MDDR), Varonis actively helps you investigate and respond to threats before they escalate.
What should I do next?
- Schedule a demo to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
- See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment.Follow us on LinkedIn, YouTube, and X (Twitter) for insights on all things data security, including DSPM, threat detection, AI security, and more.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.