Ransomware attacks are on the rise and continue to be a disruptive force in the cybersecurity industry. The FBI's Internet Crime Complaint Center reported 2,084 ransomware complaints from January to July 31, 2021. This year alone represents a 62% year-over-year increase.
To address the prevalent threat of ransomware, the Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) recently issued a Ransomware Profile, currently designated as "NISTIR 8374". Organizations can use this document as a guide to prevent, respond to, and recover from ransomware events.
Get the Free Essential Guide to US Data Protection Compliance and Regulations
What is the NIST Ransomware Profile?
NIST itself is a non-regulatory Federal agency responsible for establishing security standards for agencies and contractors - and given the evolving threat landscape, NIST is also tasked with shaping data security for the private sector.
Remember the Cybersecurity Framework (CSF), which was heavily based on NIST 800-53? Sure, you do! CSF came about because the US government wanted to give the private sector, specifically the critical infrastructure players in transportation and energy, a proven set of data security guidelines.
Now considering the apparent threat of ransomware that makes headlines daily-NIST is here to help again! The Ransomware Profile was released on September 8, 2021, and is currently in a draft stage. The profile identifies security objectives from the NIST Cybersecurity Framework and aims to help organizations identify and prioritize opportunities for improving their security and resilience against ransomware attacks.
What is the Purpose of the Ransomware Profile?
NIST 800.53 is a sprawling 400-page set of privacy security controls. To make this intimidating document more digestible for the private sector, NIST reorganized and condensed the most important controls and concepts into five functional categories: Identify, Protect, Detect, Respond, and Recover.
The Ransomware Profile aims to simplify the Cybersecurity Framework further. It breaks down the controls and offers practical steps that organizations can take to safeguard their networks from potential ransomware attacks. Organizations can utilize the report to manage the risk of ransomware and gauge their level of readiness in mitigating and responding to ransomware attacks.
Benefits of the NIST Ransomware Profile
The NIST Ransomware Profile is an excellent roadmap to covering the basics of a good ransomware resilience plan. If you establish policies and applications to cover the areas, you will be in great shape. The guidance is rooted in a data-first security perspective, which includes:
1. Identifying risks
The guidance calls for defining your digital assets and knowing what's important. This is the first step to data-first security and will help you understand where your critical data lives, and help you protect this sensitive data from breaches.
2. Putting in place security safeguards
Next, you should map your folders and permissions and implement a Zero Trust, least privilege model for your data. NIST requires that you manage who can access your critical data, and make sure you can report on who can and does access this data. An attacker's job is much easier if they only need to compromise one account to get access to your sensitive data. Do everything you can to limit access to important and sensitive data so that employees can only access what they need to do their jobs and you will significantly reduce the blast radius of an attack.
3. Continually monitoring for threats
Once you've locked down critical data, monitor and profile usage so you can alert on abnormal activity and investigate quickly. Attackers are more likely to trigger alarms if they have to jump through more hoops to access sensitive data.
4. Implementing a breach response and recovery program
Lastly, NIST requires you to have measures to respond to and recover from security incidents. If you understand where your sensitive data lives, who has access to it, and how they're using that data, it will be much easier to investigate and even stop an incident in its tracks.
Following this approach can help keep your data is safe from cyberattacks and insider threats. If you can't visualize your data risk or know when an attack could be underway, you're flying blind. If you can find and lock down important data in applications, monitor how it's used, and detect abuse, you can solve the lion's share of the problem.
How Varonis Can Help
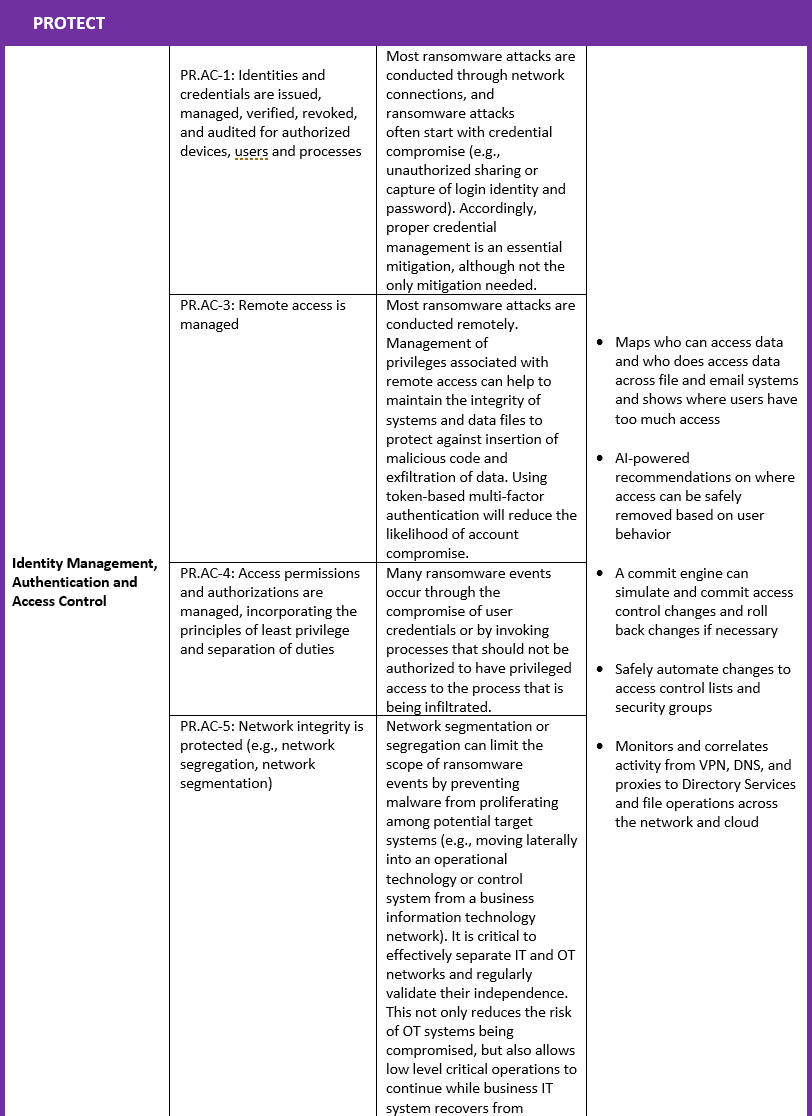
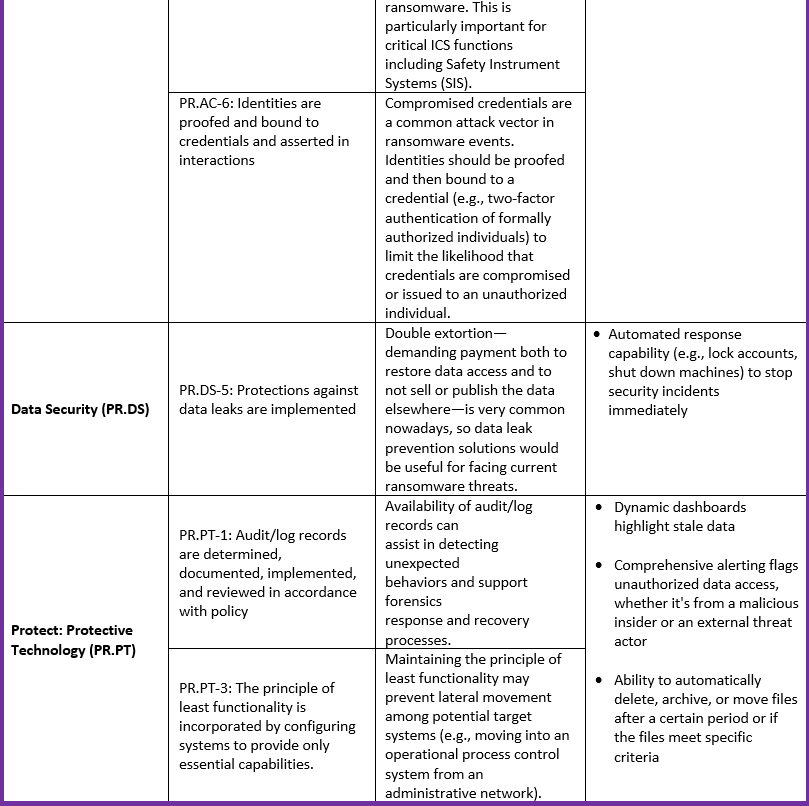
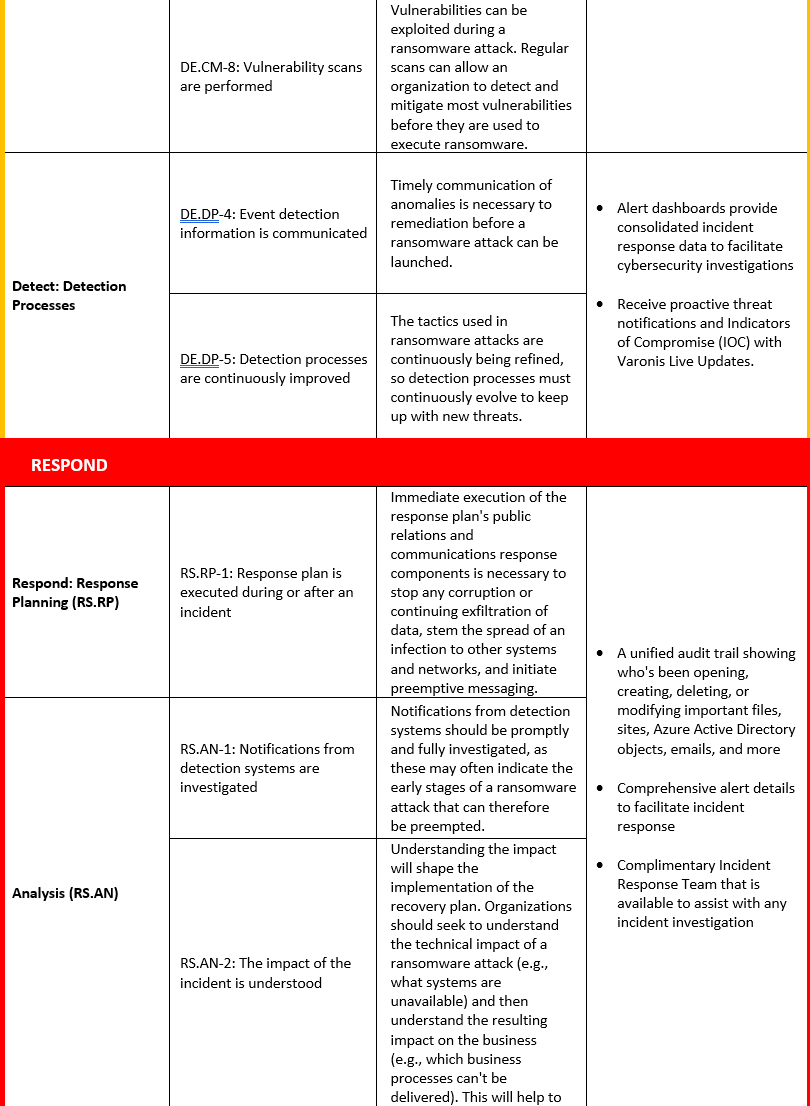
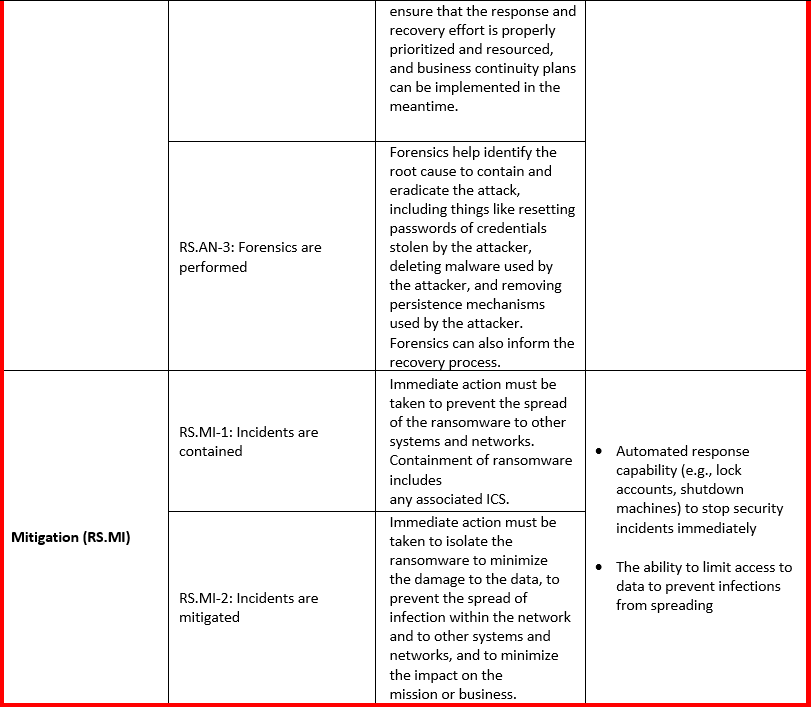
The Varonis Data Security Platform can facilitate, execute, and automate several security practices included in the NIST Ransomware Profile (as shown in the table below).
Varonis discovers sensitive data, identifies overexposure, and recommends where you can remove excessive permissions to maintain least-privileged access. This least-privilege model reduces the potential blast radius of a ransomware attack and makes it difficult for cybercriminals to infiltrate your systems.
We monitor on-premises and cloud technologies for abnormal behaviors that could signal cybersecurity incidents. Our behavior-based threat models provide high-fidelity alerts with a fully enriched, cross-platform, human-readable event log. As a result, Varonis customers can detect and stop APTs, insider threats, and ransomware with fewer false positives and faster incident response. Alerts can trigger automated responses like terminating an affected user's session or changing a password to help stop an attack in its tracks.
"We wanted to ensure that we could prevent any ransomware or malware attacks. Varonis has allowed us to do that very easily. It was demonstrated very quickly that this is a product that works."
- Ron Mark, Innovation & IT Manager, Gas Strategies
Cyber Resiliency Risk Assessment
A great first step to aligning to the NIST Ransomware Profile is a free Cyber Resiliency Assessment from Varonis. Our complimentary risk assessment run by expert forensics and incident response analysts will help you measure data exposure and stress test your security stack against the latest adversary tradecraft.
During the assessment, our team of data security experts will:
- Assess your threat detection capabilities against modern adversaries
- Classify sensitive data and measure overexposure and non-compliant access
- Document detection gaps, Zero Trust posture, and remediation priorities
- Prepare and educate your team to handle advanced incidents
The results are yours to keep, with no strings attached.
How Varonis Maps to the NIST Ransomware Profile
Varonis puts data first, watching and securing what attackers want most. To truly minimize the blast radius of a ransomware attack, organizations have to understand their data-what data's sensitive, who can access it, and how they're using it. With this approach, ransomware can't hide.
The following table maps the relevant NIST CSF Ransomware Profile principles to Varonis' capabilities:
-png.png)
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








