Around this time each year, you’ll start to notice various publications releasing articles authored by experts and SMEs that outline the “Yearly Cybersecurity Trends to Watch” or similar topics.
Although I recognize that some technologies are constantly advancing (an observation that became particularly apparent after I upgraded my 17-year-old SUV to a brand-new hybrid last month), I was curious to see how macroeconomic cybersecurity trends have evolved over recent years.
Comparing cybersecurity trends: 2018 vs. 2025
To this end, I conducted my own “scientific study” online (which, as my two teenagers say, if it’s on the internet, it must be true). I used two search engines to analyze the first non-sponsored summarized results for the prompts "2018 Cybersecurity Trends to Watch" and "2025 Cybersecurity Trends to Watch".
Search engine: Microsoft Bing
Prompt: "2018 Cybersecurity Trends to Watch"
Top result: "7 Cybersecurity Trends to Watch out for in 2018"
Trends:
- AI-powered attacks
- More sandbox-evading malware
- Ransomware and IoT
- Many companies will fail to comply with the GDPR
- Emerging standards for multi-factor authentication
- The adoption of more sophisticated security technologies
- A rise of state-sponsored attacks
Prompt: "2025 Cybersecurity Trends to Watch"
Top result: "The Top Cybersecurity Trends to Watch in 2025"
Trends:
- Rise of AI and machine learning in cybersecurity
- Increased focus on Zero Trust security models
- Evolution of ransomware attacks
- Growth of cloud security concerns
- Quantum computing and its impact on cryptography
- Expansion of cybersecurity skills gap
- Privacy and data protection regulations
- The rise of cybersecurity mesh architecture (CSMA)
Search engine: Google
Prompt: "2018 Cybersecurity Trends to Watch"
Top result: "Cybersecurity Trends for 2018"
Trends:
- An adversarial machine learning “arms race” between attackers and defenders
- Ransomware to evolve from traditional PC extortion to IoT, high net-worth users, and corporate disruption
- Serverless apps to create attack opportunities targeting privileges, app dependencies, and data transfers
- Connected home devices to surrender consumer privacy to corporate marketers
- Consumer apps collection of children’s content to pose long-term reputation risk
Prompt: "2025 Cybersecurity Trends to Watch"
Top result: "The Top 25 Security Predictions for 2025 (Part 1)"
Trends:
- "Agentic AI" emerges as a hot new opportunity for everyone — and also a potential new cyber threat vector
- AI-driven scams and social engineering will surge
- Ransomware evolves with automation and AI
- Supply chain attacks on the rise
- Democratization of cyber crime tools
- Geopolitical cyber warfare intensifies
- Post-quantum threats accelerate
- IoT and edge devices as growing attack vectors
- AI-powered SOCs and automation will redefine defenses
- Regulatory pressures and compliance shifts
My initial perspective was that the results were unsurprising. While the information is accurate, the authors' motivations and experiences likely differ. Despite our efforts to be objective, bias is inherent in everyone.
What I did find interesting was that data security wasn’t mentioned as a trend to watch in either year, even though implementing a cohesive Zero-Trust architecture is an essential cybersecurity strategy and a requirement for our federal government.
The importance of data security
Why is data security so critical? Simply put, regardless of attackers, their TTPs, or their motives — be it malicious insiders, financially motivated criminals, or nation-states — data is always the target.
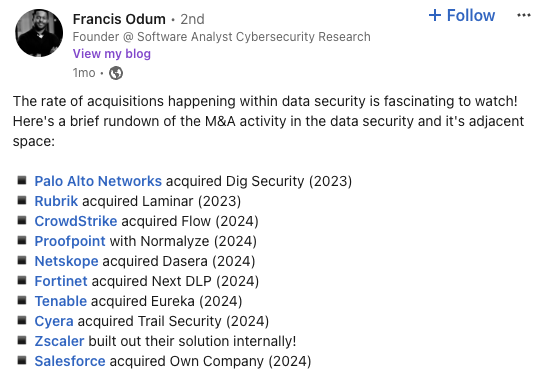
Francis Odum’s recent LinkedIn post succinctly summarized the interest in data security. He stated, “The rate of acquisitions shows companies are ‘racing’ to enhance their offerings and provide holistic protection for sensitive data with the rise of AI.”
Just as major corporations are scooping up smaller data security firms due to their profitability, this can be compared to Willie Sutton, one of the first fugitives on the FBI Top Ten list, who famously said he robbed banks "because that's where the money is."
Joe Kim of Squadra Solutions puts it this way: “While there’s been a lot of progress in securing identity, networks, and endpoints, data security has often been pushed to the back burner. But at the end of the day, data is the core asset Zero Trust is designed to protect.”
The future of cybersecurity
The focus for 2025 and beyond should be on protecting data. The industry has invested billions in cybersecurity to protect critical information, but we’ve always concentrated on protecting the perimeter rather than the data itself.
Defensive cyber operations aim to protect national security, privacy, personal information, and intellectual property. However, this has been challenging based on previous approaches.
A paradigm shift is needed, with Zero Trust serving as the catalyst for this change. This doesn’t mean we ignore any of the trends outlined above.
Instead, it suggests that we need to reassess our approach by focusing on protecting sensitive information from an “inside-out” perspective. This will ensure that we remain one step ahead of our adversaries and achieve the security outcomes we expect.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.