To secure data, you need to know where it is, what kind of data it is, and if it’s at risk. While there are many considerations when evaluating data discovery and classification, one of the most important — and most overlooked — is how the data is scanned.
There are two main ways for scanning data: full SaaS data transfer and collector-based scanning. Full SaaS data transfer is the most direct way to scan data while collector-based scanning offers the greatest privacy, security, and control.
In this blog, we’ll describe how each method works and why you should think carefully when choosing between full SaaS data transfer and collector-based scanning.
Full SaaS data transfer
For a full SaaS data transfer, the security solution connects directly to the customer’s account via API. Samples of the customer data are transferred directly from the customer account to the provider’s cloud to be classified.
While full SaaS data transfer is the simplest way to scan data, it does come with some concerns: privacy risk, increased attack surface, and loss of control.
- Privacy risk: Data transfer across jurisdictions can violate a litany of data privacy regulations, including GDPR, CCPA, and HIPAA. Companies that are subject to these regulations must ensure that data is stored within a specified physical or geographic location. For companies that are subject to these regulations, SaaS-to-SaaS data transfers might be a non-starter.
- Increased attack surface: By centralizing sensitive customer data, the security vendor itself could become a target. Security solution providers that consolidate sensitive data become data risks themselves and could put their customer's data at risk.
- Less control: With full SaaS data transfer, your security teams no longer have full control over the data. They need to be comfortable trusting that a third-party vendor (and all of their third-parties—think SolarWinds) will safeguard their sensitive data, especially if they are feeling your data to AI models.
Collector-based scanning
Collector-based scanning deploys a collector (sometimes called an "outpost") within the customer’s cloud or data center. The classification and analysis of sensitive data takes place in the customer's environment. Only metadata and logs are transferred.
The key benefits of collector-based scanning are:
- Data sovereignty: The customer maintains full control of where sensitive data resides. Data never leaves approved environments and compliance is greatly streamlined.
- Reduced attack surface: If the security provider is targeted by a cyberattack, the customer data remains protected. Your attack surface doesn’t expand with the security tools you are seeking to implement.
- Control: The customer is in full control of their data. There is never any question about the provider's practices or the security and privacy of transferred data.
- Efficiency: Scanning happens in near real-time when done in close proximity to where the data resides. Customers avoid the bandwidth costs and latency associated with sending terabytes of data per hour over a WAN to the vendor's cloud for scanning.
Varonis offers both collector-based scanning and full SaaS data transfer for data discovery and classification.
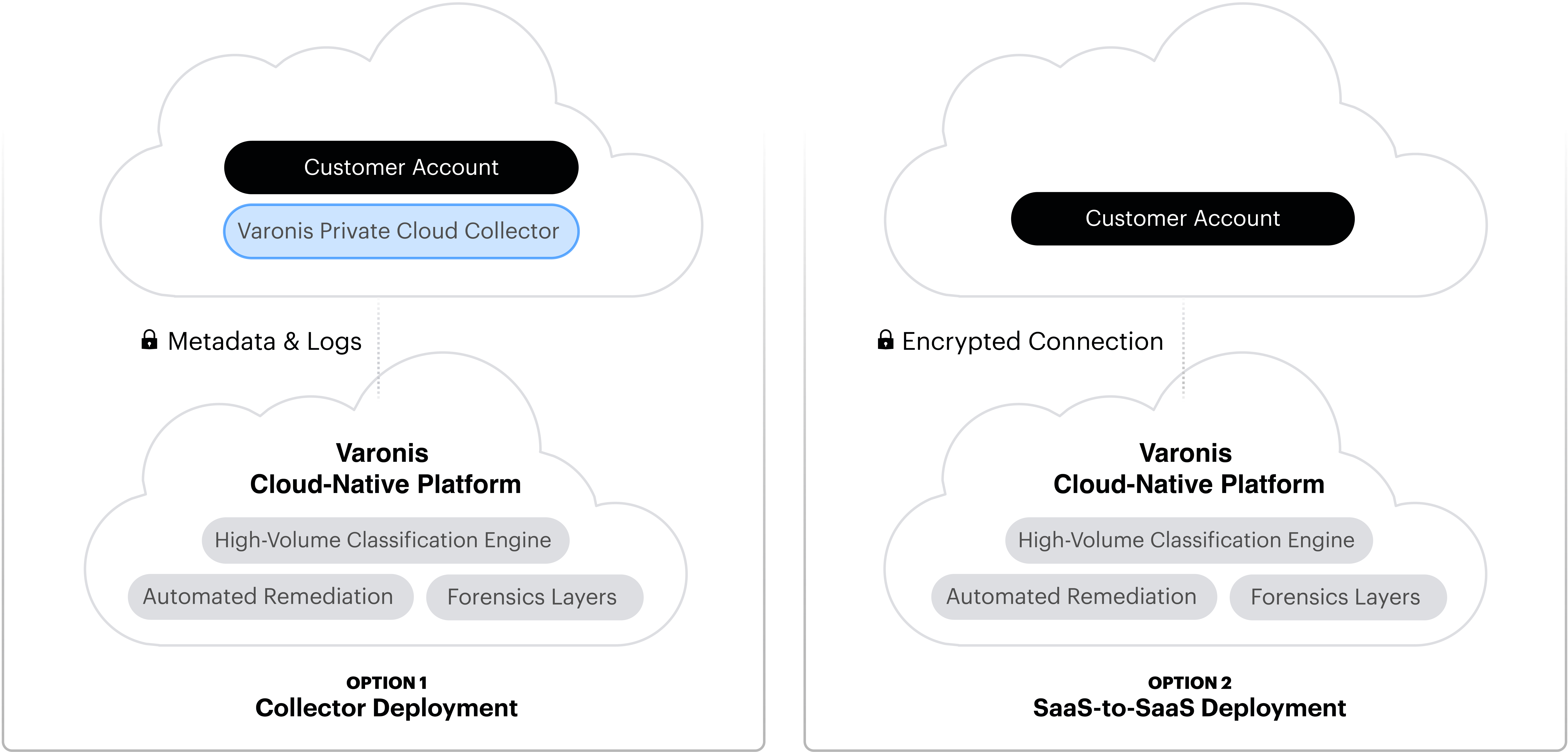
Varonis offers both collector-based scanning and full SaaS data transfer for data discovery and classification.
The Varonis Private Data Collector
Varonis offers both full SaaS data transfer and collector-based scanning providing the simplest and most secure ways to classify data. The Private Data Collector offers all the benefits of collector-based scanning – data sovereignty, reduced attack surface, and control – with the added benefit of real-time, complete, and optimized scanning.
Setting up the Private Data Collector is fast and can be done from the Varonis UI in a few simple steps. Once set up, the collector performs classification in the customer environment, in-memory. No data is retained within the collector.
The collector automatically optimizes the resources needed for classification, ramping up and down processing based on the classification queue. This allows Varonis to classify all a customer’s data in real time. There is no need to resort to sampling or periodic scans that miss critical data and risks. The Private Data Collector sends the result metadata of the classification scans back to the Varonis environment in real time.
The Varonis Private Collector doesn't transfer data from the customer's environment. Instead, the data is classified within the customer's environment, providing data sovereignty, reducing the attack surface, and increasing control.
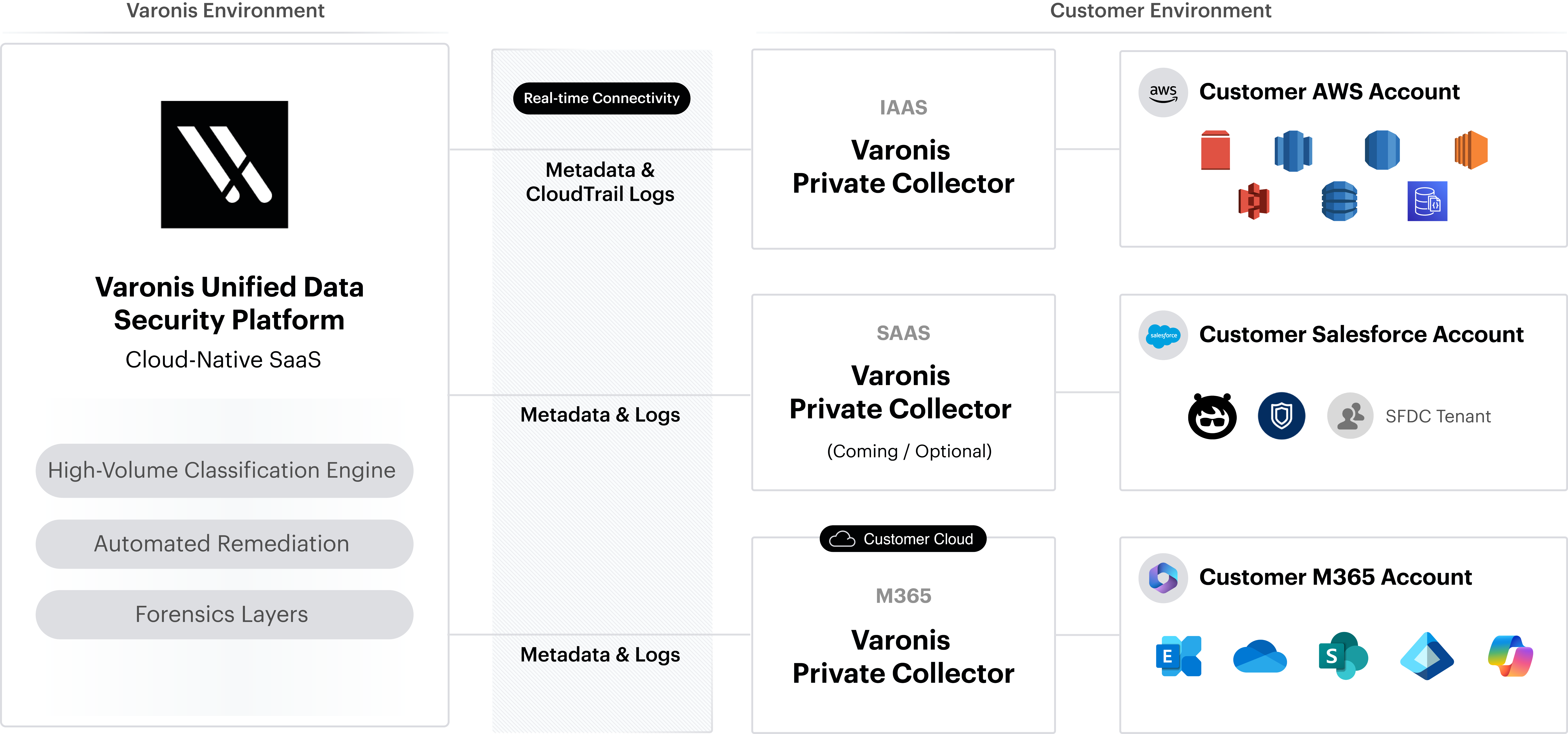
The Varonis Private Collector doesn't transfer data from the customer's environment. Instead, the data is classified within the customer's environment, providing data sovereignty, reducing the attack surface, and increasing control.
How data is scanned matters
While there are good reasons for choosing both ways of scanning data, it’s important to understand which method best suits your organization’s requirements when evaluating a DSPM or data security platform. Full SaaS data transfer is simple and direct, while collector-based scanning offers the most secure way to scan data.
Enhancing your data security
Varonis' Data Security Platform is designed to help safeguard sensitive information within organizations. With unparalleled real-time data classification and risk mitigation capabilities, Varonis ensures that no critical data is overlooked. The Private Data Collector optimizes the scanning process and provides immediate feedback, allowing you to act swiftly to secure your environment.
Don't compromise on data security. Choose Varonis for comprehensive, real-time classification and robust risk mitigation. Take control of your data protection today and safeguard your organization's future.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.