A series of vulnerabilities in CUPS were recently disclosed by Simone Margaritelli, who is known as “evilsocket” on X (Twitter). OpenPrinting CUPS (Common UNIX Printing System) is an open-source printing software that is often included by default in various Linux distributions.
What does this mean for my organization?
When chained together, evilsocket shared that these vulnerabilities allow a remote, unauthenticated attacker the ability to install a malicious printer (or hijack an existing one), resulting in arbitrary code execution as the ‘lp’ user when the server receives a print job.
When abused together, these vulnerabilities provide an attack vector for Remote Code Execution (RCE), one of the worst possible consequences for a vulnerability.
This disclosure appears to have happened suddenly and ahead of its scheduled October 6 release.
The researcher attached a list of 2,899 Linux versions to their ongoing X thread, with the implication that these represent all versions impacted by default due to the installation of OpenPrinting CUPS being present.
The vulnerabilities appear to belong to various components of CUPS, including:
- cups-browsed [https://github.com/OpenPrinting/cups-browsed]
- libppd [https://github.com/OpenPrinting/libppd]
- libcupsfilters [https://github.com/OpenPrinting/libcupsfilters]
- cups-filters [https://github.com/OpenPrinting/cups-filters]
Details of the leak
In a leak on BreachForums from September 24, the following GitHub advisory posts relating to the vulnerabilities were shared.
- https://github.com/OpenPrinting/cups-browsed/security/advisories/GHSA-rj88-6mr5-rcw8
- https://github.com/OpenPrinting/libcupsfilters/security/advisories/GHSA-w63j-6g73-wmg5
- https://github.com/OpenPrinting/libppd/security/advisories/GHSA-7xfx-47qg-grp6
- https://github.com/OpenPrinting/cups-filters/security/advisories/GHSA-p9rh-jxmq-gq47
The leak also suggested the criticality of the vulnerabilities is extremely high. With evilsocket responsible for the research, we concluded that the leak is credible, and the above links do point to the still-private advisories.
Relevant CVEs
According to evilsocket, the relevant CVEs include:
- CVE-2024-47176 | cups-browsed <= 2.0.1 binds on UDP INADDR_ANY:631 trusting any packet from any source to trigger a Get-Printer-Attributes IPP request to an attacker controlled URL.
- CVE-2024-47076 | libcupsfilters <= 2.1b1 cfGetPrinterAttributes5 does not validate or sanitize the IPP attributes returned from an IPP server, providing attacker controlled data to the rest of the CUPS system.
- CVE-2024-47175 | libppd <= 2.1b1 ppdCreatePPDFromIPP2 does not validate or sanitize the IPP attributes when writing them to a temporary PPD file, allowing the injection of attacker controlled data in the resulting PPD.
- CVE-2024-47177 | cups-filters <= 2.0.1 foomatic-rip allows arbitrary command execution via the FoomaticRIPCommandLine PPD parameter.
Identifying exposure
Our research suggests that running any version of the CUPS software prior and equal to the latest (<=2.0.1) is vulnerable to the chain of attack.
In order to fully exploit the chain of vulnerabilities, a server must be running the CUPS Service. This can be determined by using ‘lpstat -r’.
If you see ‘scheduler is running’, then CUPS is likely running on the server, since ‘lpstat’ is used to display the status of the CUPS service, among other items.
It is likely the server is vulnerable to the attack chain if this is enabled and any of the outlined versions are deployed.
The attacker must be able to reach the active CUPS port (by default 631) via UDP. If your server is behind a firewall blocking this over the internet, then that would prevent external attackers from exploiting this attack chain. However, it would still be vulnerable internally or wherever UDP 631 can be reached.
A Shodan search attempting to identify CUPS/ servers on the internet revealed around ~90 thousand servers. evilsocket has mentioned finding upwards of 300,000 over the past few weeks.
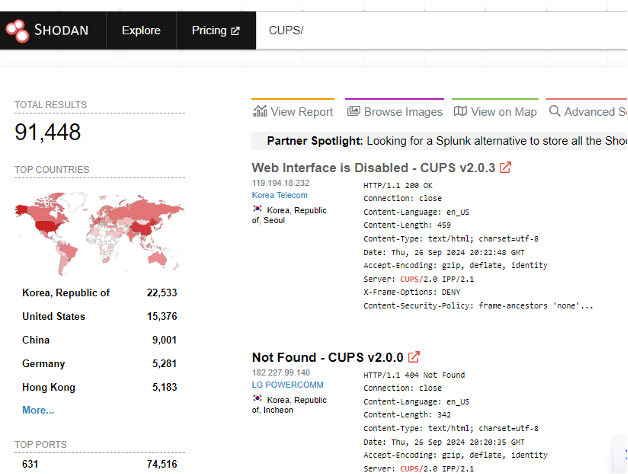
A Shodan search attempting to identify CUPS/ servers on the internet revealed around ~90 thousand servers. evilsocket has mentioned finding upwards of 300,000 over the past few weeks.
Mitigating impact
Per evilsocket, the below are recommended as mitigations/remediation measures:
- Disable/Remove cups-browsed service
- Update the CUPS package on your systems.
- Block all traffic to UDP port 631 and DNS-SD traffic
Another potential mitigation is to edit the cups-browsed configuration file (located at /etc/cups/cups-browsed.conf) to prevent connections from unwanted sources by setting up host or network-based “allow and block lists” for your CUPS servers as required.
Stay updated with Varonis.
Our research team is working on identifying indicators of exploitation that can help your team determine if this specific chain of attack was used against one of your Linux devices.
Currently, the best indicator appears to be monitoring CUPS printers for any new printers being installed or existing printers being modified. ‘lpinfo -v’ (deprecated) will list all detected printers and ‘lpstat -v’ will list all printers and the device they are attached to.
Our team will update this blog post with new information as it is released. If you need additional assistance securing and monitoring your data, please reach out to our team.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.



-1.png)




