Salesforce complexity breeds risk and creates headaches for admins. With complicated Profiles, Roles, Permission sets, and Groups, it is incredibly difficult and time-consuming to understand what a user can and cannot do in the CRM tool.
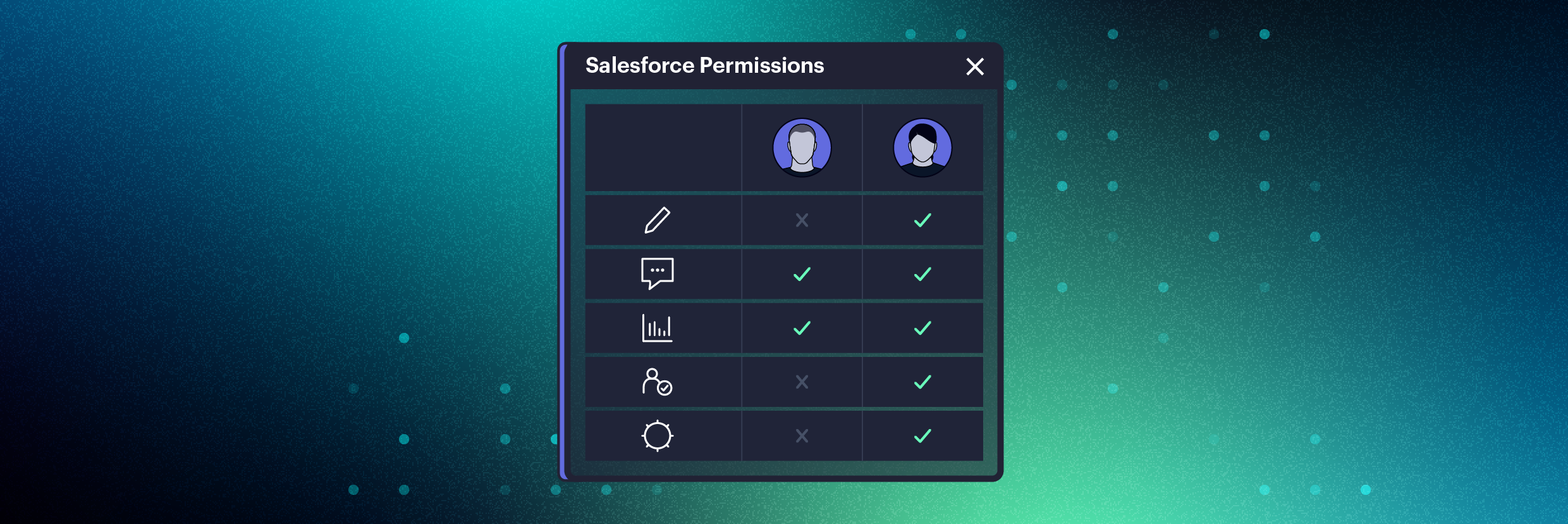
With the new permissions comparison feature in Varonis DatAdvantage Cloud, we’re taking hours of work off Salesforce admins’ plates. With the click of a button, admins can compare two users’ aggregated permissions side-by-side and quickly identify discrepancies. You can even compare permissions across different Salesforce orgs — a game-changer for teams handling mergers and acquisitions.
 (Compare two Salesforce users’ permissions side by side)
(Compare two Salesforce users’ permissions side by side)
Get a Free Data Risk Assessment
Analyzing permissions in Salesforce
To understand what a user can do in Salesforce using only Salesforce’s native tools, CRM admins must take into account the permissions a user was granted through their Profile and add up the different Permission Sets and Permission Set Groups to get their effective permissions. Yowza.
To add to the complexity, admins can mute (exclude) specific permissions when they assign permission sets to a user. And all of that is just so admins can understand what tables and fields users can access. Figuring out what records a user can read, and edit is a whole other can of worms.
 (System Permissions configuration in Salesforce)
(System Permissions configuration in Salesforce)
To determine a user’s record-level permissions, you need to review your org-wide defaults (i.e., can anyone access/edit a new record, or can only the creator) and analyze where the user sits within the organizational hierarchy.
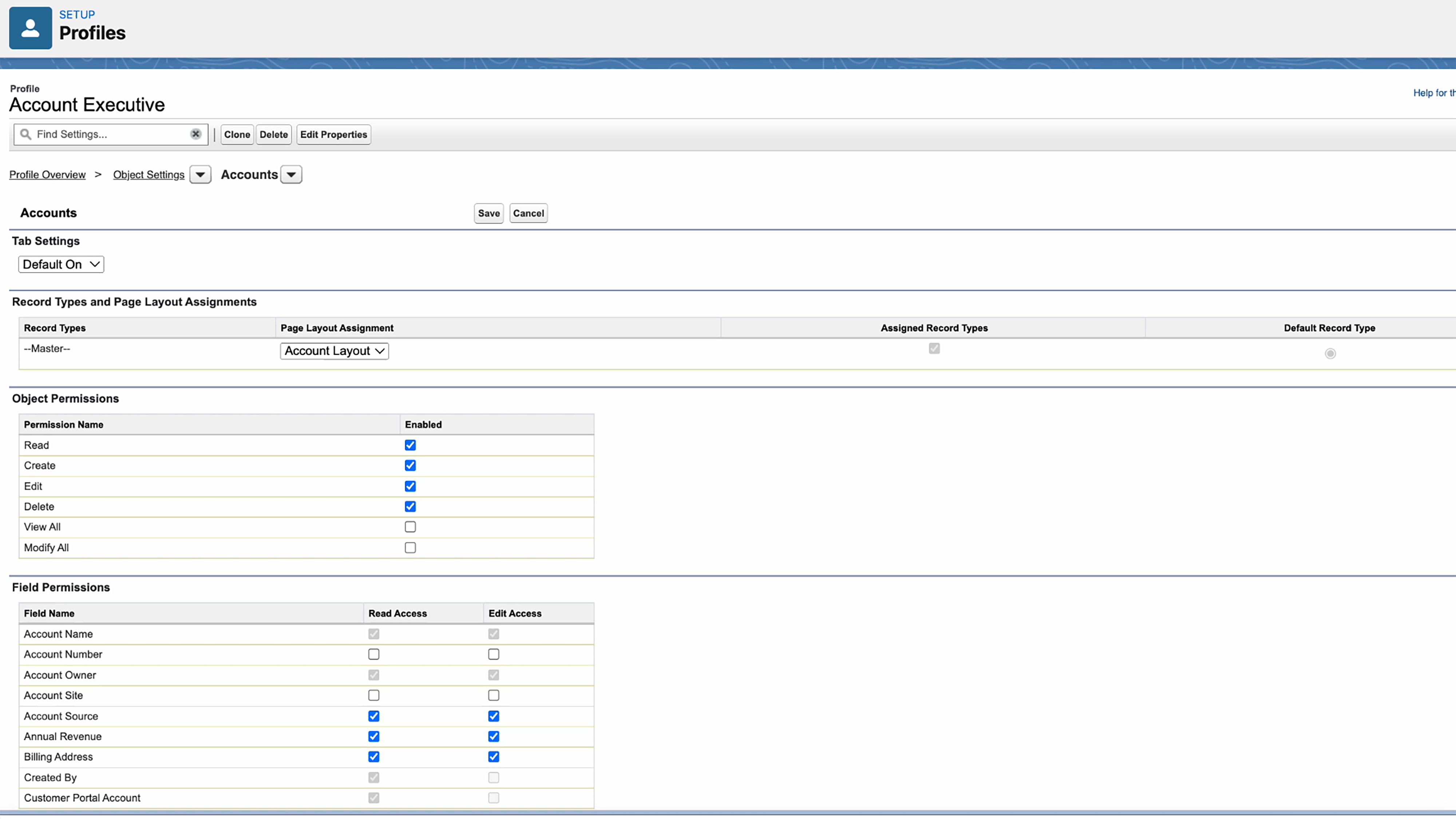 (Object and field permissions configuration in Salesforce)
(Object and field permissions configuration in Salesforce)
By default, a manager can access and edit records that their employees or anyone else below them hierarchically can access.
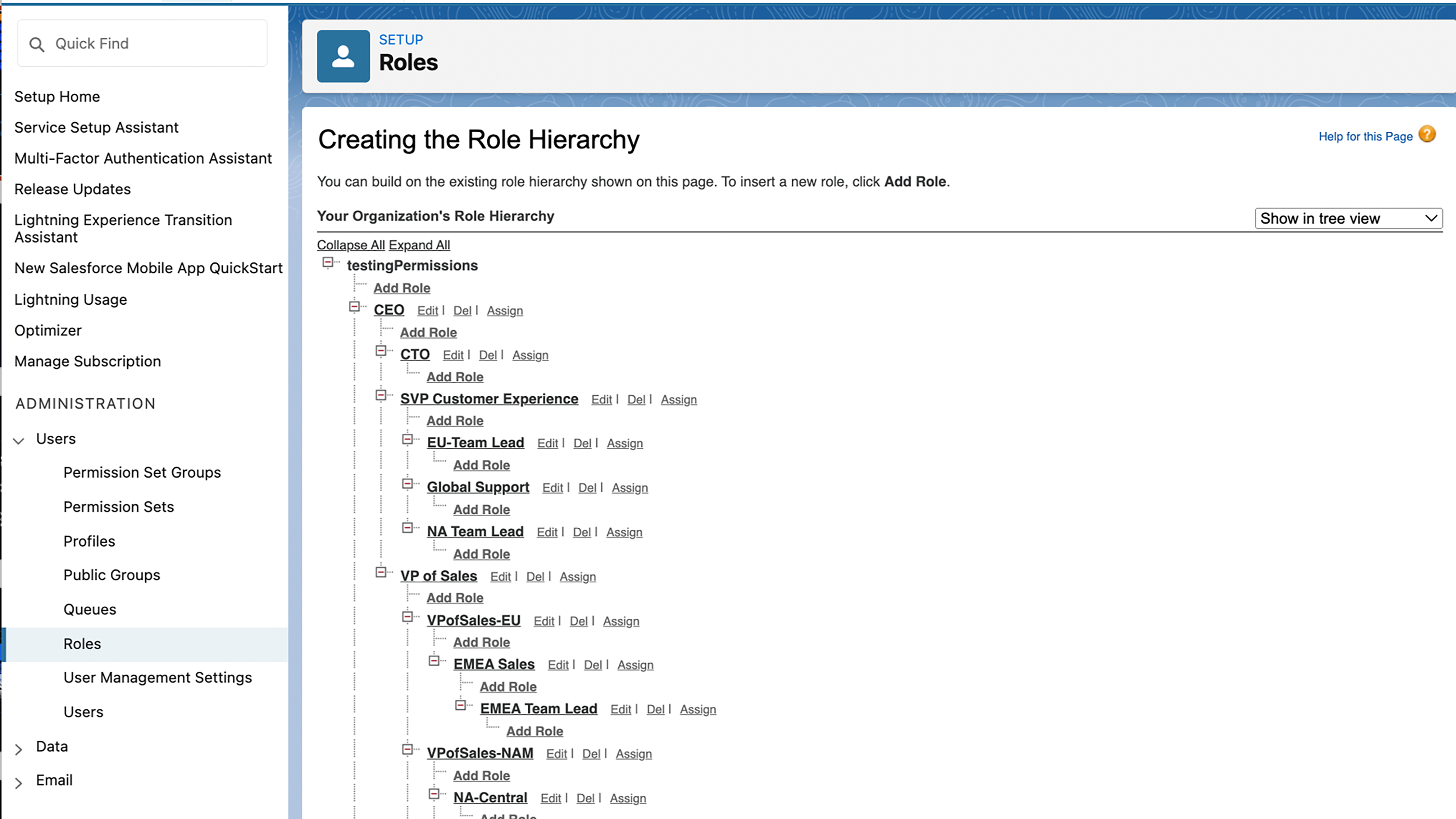 (Role Hierarchy settings in Salesforce)
(Role Hierarchy settings in Salesforce)
The process of going through each of these nested screens and keeping track of each of the settings (using Excel, for example) can take CRM admins hours.
Now try and compare one user’s effective permissions with another user. Even if you have this information kept on hand, there’s a good chance something has changed since the last time you reviewed their permissions, and so you’ll probably need to re-compile that data again to be safe. By only using Salesforce’s native tools alone, you’ve created an unsustainable process.
Simplify permission analysis and comparison with Varonis.
Varonis radically simplifies analyzing permissions in Salesforce, displaying a user’s net effective permissions + how they were obtained, all on one screen.
Instead of clicking into every user’s Profile, then clicking into every single one of their Permission Sets, you can see all user effective permissions in one place.
(Analyze system permissions in DatAdvantage Cloud)
Go deep into object and field-level permissions.
On top of system-level permissions, Varonis extends visibility to the object and field level. We simplify access into a simple CRUDS model (create, read, update, delete, share) and show you exactly what level of access someone has to every field and record in your environment.

(Analyze field and object level permissions in DatAdvantage Cloud)
With this new update from Varonis, Salesforce admins can go a step further and compare two users’ permissions from the same screen as we demonstrated above.
Become a Salesforce hero
Interested in learning who can access your Salesforce data and why? It only takes 15 minutes to get started with Varonis DatAdvantage Cloud. Schedule your risk-free demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.


-1.png)