Let’s face it people, we’re bad at coming up with our own passwords. They’re too short, too obvious, and hackers have gotten very good at breaking them —either by outright guessing or looking up password hashes in large pre-computed tables.
How bad is our collective password making abilities? You can see for yourself. After the epic RockYou data breach in 2009, 32 million unencrypted—I had trouble with that as well –passwords were stolen and made available on the Intertoobz.
Hate computers professionally? Try Cards Against IT.
We now have a pretty good idea just how uninspired the general public is at this essential security task.
The Evils of Convenience
Not surprisingly, “123456” was the most popular—it was the choice of almost 300,000 users—followed by all the usual suspects: “password”, “iloveyou”, and the name of the online gaming service itself, “rockyou”.
Convenience is, understandably, driving our password choices. After looking through the RockYou files myself, I can say you’re not being the least bit clever using this formula: <your name> + “boy” or “girl”+ <random two digit number>.
Hackers exploit our desires for convenience, and so they can make very informed high-probability guesses.
It’s only a little more complicated if they get a hold of a list of password hashes, as was the case of infamous Linkedin breach. Using existing password lists and dictionaries of common words, they can pre-compute giant tables associating passwords with hash values. After a quick reverse lookup, they’ve broken the cryptic hash sequence.
Yes, “salting” the hashes helps, but with immense computing power within reach of average hackers, offline brute force attack are now feasible.
By the way, Cindy and I are finishing up an ebook that examine the many issues with password-based authentication, including an in-depth look at password hashes. We’ll have more news very soon!
Longer Is Better
One very obvious way to make the job of hackers more difficult is to come up with longer passwords—in crypto-speak, you’re increasing information entropy.
Why does adding a few characters to a password make such a difference? It’s really has to do with the power of exponential growth.
Let’s say your choice of characters includes upper and lower case letter (52 possibilities), numbers (10), and all those punctuation and other non-alpha numeric symbols (about 13). If you add it up, then increasing the password by a single character introduces 75 new possibilities.
A six character password means that the total number of combinations is 75 raised to the power of six, which is over 200 billion. In the Big Data era, this ain’t a large number. Add two more characters, and the space that hackers have to search is now almost a quadrillion—a thousand trillions.
Longer passwords, say in the 8-10 range, push guessing attacks into the unlikely-to-succeed zone. Hackers who’ve obtained a file of password hashes would have a serious computation problem on their hands.
Easy Long Passwords
It turns out we humans are capable of coming up with long passwords. The technique I now present is based on an old-fashioned memory trick, known as a mnemonic.
The idea is you create a story and then use that to generate the letters and symbols. For example, I know on Saturdays, I usually have a lot of errands to do. So here’s the story that I use: Every Saturday, I go to the dry cleaners at 10 to get my 2 sweaters.
From that sentence I take the first letter of each word to create my long, non-crackable password: ES,Igttdca10tgm2s. I would never remember that long string on its own. But with my little story, which is easy for me to recall, I can quickly recreate the password.
Yes, you can be creative, and your stories can involve sports teams and scores, or shopping lists and recipes.
So your assignment is to make a New Year’s resolution to change all your passwords in January 2015.
Or SyaitmaNY’srtcaypiJ2015.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.

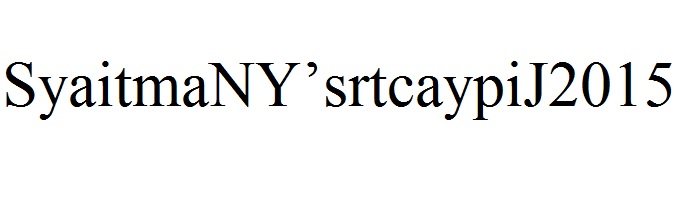


![are-you-smarter-than-a-hacker?-[contest]](https://www.varonis.com/hubfs/Imported_Blog_Media/varonis-default-featured-image-Aug-20-2021-06-54-28-74-PM.jpg)

