A solutions architect at a regional bank was concerned about data security. His company decided to go all-in on AWS, and while the org was excited, he was concerned about his IT team’s ability to scale data security in the cloud.
His concern was valid. In constantly changing cloud environments, too much data is stored in too many disparate places with too many attack vectors for manual remediation.
Data security posture management (DSPM) has emerged as a standard for securing sensitive data in the cloud and other environments, but without automation, DSPM doesn’t stand a chance. Instead of helping to secure data, IT teams are left with an ever-growing list of issues to investigate and remediate — and inevitably, they fall behind.
In this post, we’ll delve into the challenges of securing data in the cloud, explain why automation is crucial to overcoming those challenges, and share what an automated DSPM approach should look like.
One misconfiguration puts millions of identities at risk.
Even one security lapse in cloud environments puts your sensitive data at risk.
For example, a healthcare company that uses AWS mistakenly exposed millions of clinical records after changing a security rule, leaving a PostgreSQL database open to the public. This left the data inside the database vulnerable to malicious attacks, which could have resulted in millions of clinical records falling into the wrong hands, millions of fraudulent medical claims, or even millions of stolen identities.
When one misstep can be catastrophic, IT and security teams need to be vigilant about securing their cloud data, but that's easier said than done.
The flexibility of the cloud breeds risk.
Cloud environments or IaaS providers like AWS, Microsoft Azure, and Google Cloud provide developers tremendous flexibility, but that flexibility comes with risk.
Data in the cloud is a prime target for attackers. A recent study found that it takes just eight hours to breach a misconfigured or unsecured database, and in 2023, more than 80 percent of data breaches included cloud data.
Many organizations use multiple clouds with large, sometimes outsourced, development teams constantly spinning up resources. The proliferation of databases, object storage, and now AI training pipelines contribute to the data sprawl.

The flexibility of the cloud creates the risk of a data breach.
Because of this complexity and continuous change, hundreds of potential attack paths now exist.
Organizations must be aware of misconfigurations, overly permissive access, shadow databases, and more. Each attack path can be exploited quickly, and generative AI makes it even easier to access sensitive data.
For example, a bad actor can access sensitive data by simply asking a gen AI copilot questions. They don’t need to understand the environment or even what data they can access. Because of this, gen AI copilots are an easily exploited attack vector.
Securing data in the cloud requires automation.
Without automation, IT and security teams fall behind.
IT and security teams struggling to keep up with increasing cloud risk may look for a solution to ease their burden, but most tools stop before the last mile — and end up creating more work.
Discovery-only tools find sensitive data but provide little visibility and control over exposure. Infrastructure tools focus on the configurations of the buckets and containers but lack context about your data security. And many DSPM tools take a passive approach, providing some visibility into sensitive data and a limited understanding of exposure, but stop there.
Passive DSPM either offers no remediation or requires complicated third-party ticketing workflows to delegate remediation tasks. The result is a long list of issues to investigate and fix manually. As one CISO said about their experience with a passive DSPM solution, “I started with one problem and ended up with 50,000.”
What is automated DSPM?
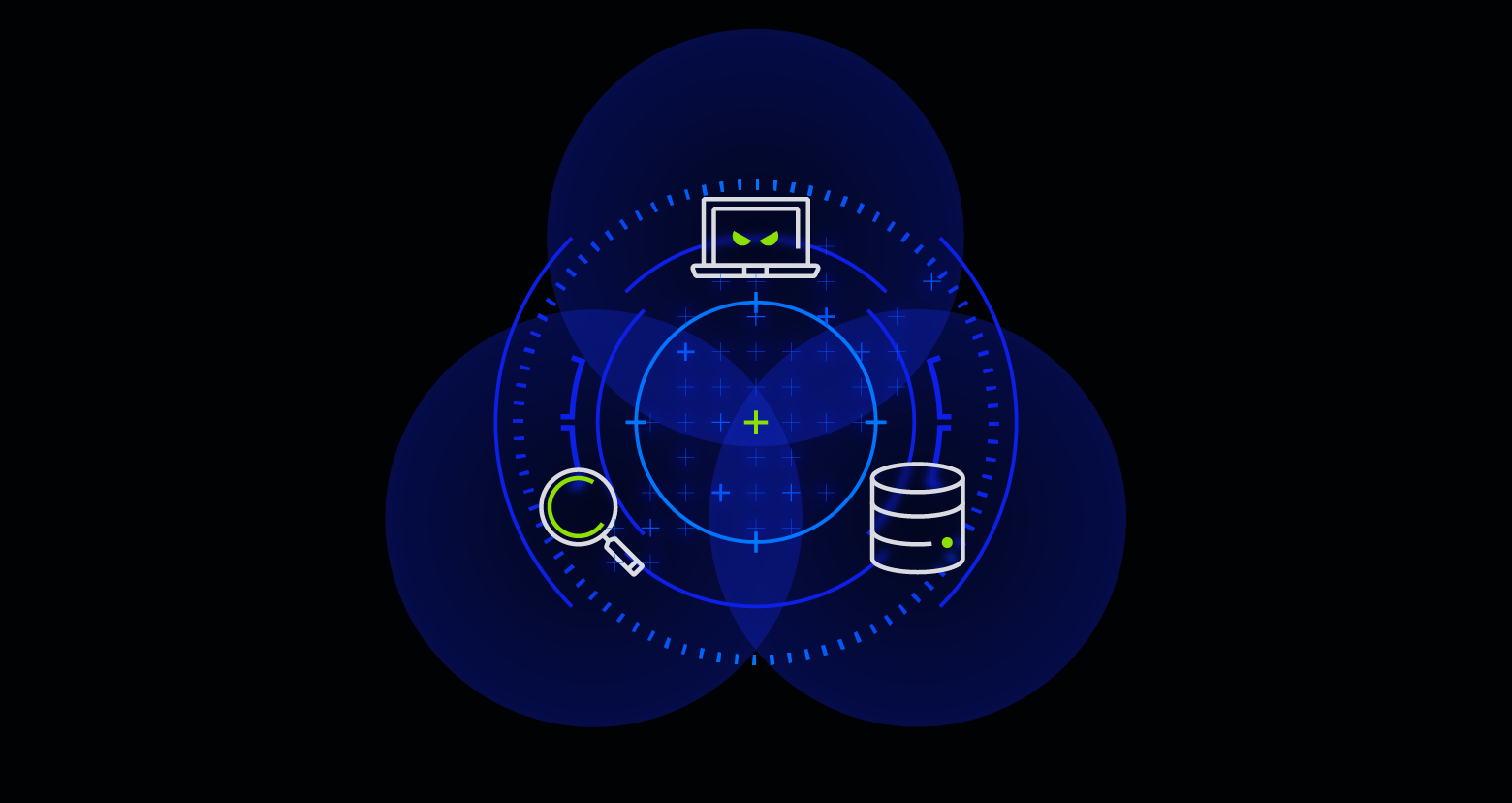
Automated DSPM gives you the necessary visibility to understand your data and its exposure, helping you remediate issues and detect threats automatically. Automated DSPM requires three elements:

Automated DSPM requires three sets of capabilities.
Complete, real-time visibility
Automatically and continuously scan your environment to understand your sensitive data, who has permission to access the data, and their identities. This provides an audit log of how and by whom data is being used.
These scans need to be real time. Cloud environments change fast, and exposure doesn’t take long to become a breach. Relying on sampling or periodic scans will leave your data open to an attack.
Automated remediation
Once you understand your data and its exposure, you must quickly fix issues and close vulnerabilities before they are exploited. Without automation, this quickly becomes a losing battle.
Automated remediation helps you avoid vulnerabilities and creates a secure environment by automatically fixing issues such as revoking excessive access and enforcing encryption.
Proactive threat detection
When securing data in the cloud, threat detection is vital to identifying active intrusions, such as stealthy attacks and insider attacks, while monitoring full coverage of the kill chain.
Secure your cloud data.
Any cloud-first organization looking to get ahead of the curve and create a more secure environment should look to automated DSPM.
Varonis leads the DSPM market on Gartner Peer Insights and is the only solution that automatically remediates risk, enforces policies, and detects threats in real time.
Explore automated DSPM and schedule a 30-minute demo to learn more.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.





.jpg)