
Neil Fox
Neil is a cyber security professional specializing in incident response and malware analysis. He also creates cyber security content for his YouTube channel and blog at 0xf0x.com.
-
 Data Security
Data SecurityApr 12, 2022
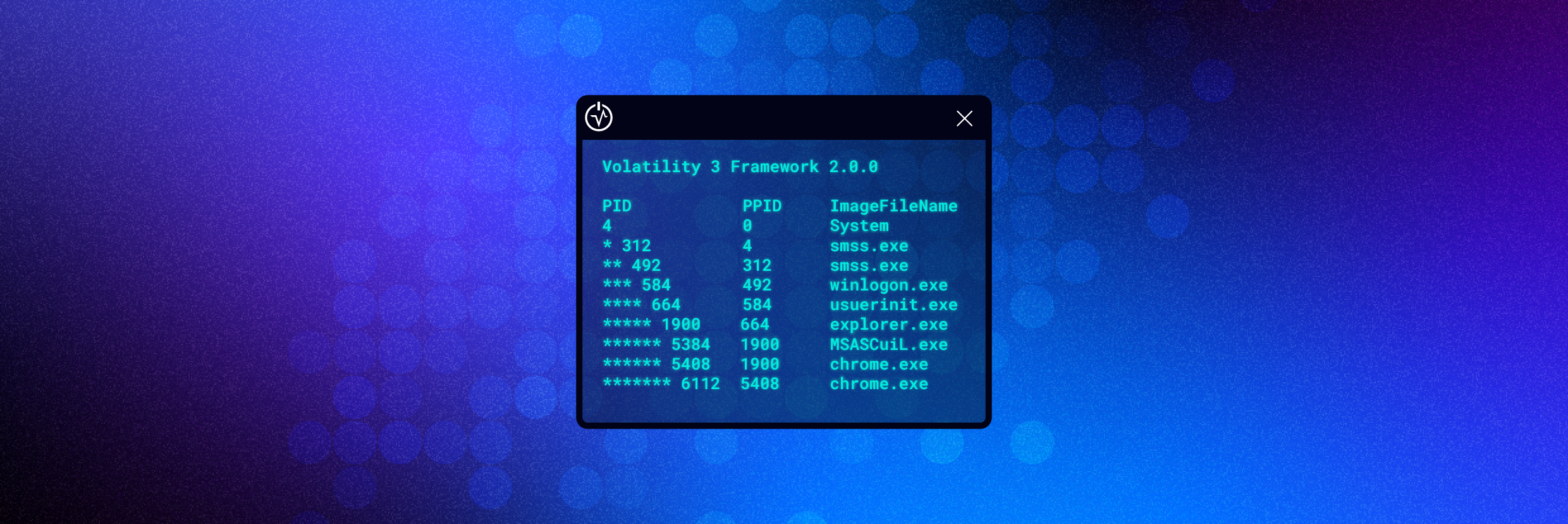
How to Use Volatility for Memory Forensics and Analysis
This article will cover what Volatility is, how to install Volatility, and most importantly how to use Volatility.

Neil Fox
8 min read
-
.jpg) Data Security
Data SecurityMar 21, 2022
How to Use Ghidra to Reverse Engineer Malware
An overview of the malware analysis tool Ghidra. This article covers how to install and navigate the Ghidra interface.

Neil Fox
7 min read
-
 Data Security
Data SecurityFeb 25, 2022
Common Types of Malware
This piece covers the various types of malware that are available and their characteristics.

Neil Fox
7 min read
-
 Data Security
Data SecurityOct 06, 2021
PeStudio Overview: Setup, Tutorial and Tips
An overview of the free malware analysis tool PeStudio.

Neil Fox
6 min read
-

Jul 26, 2021
Memory Forensics for Incident Response
When responding to a cybersecurity incident I’ve always found memory forensics to be a great skill to have. By capturing the memory of a compromised device you can quickly perform…

Neil Fox
6 min read
-
 Data Security
Data SecurityJun 02, 2021
Process Hacker: Advanced Task Manager Overview
This article is an overview of the tool Process Hacker. This is a popular tool amongst security professionals when analyzing malware as it will display real-time activity of processes and provide a wealth of technical information on how a particular process is behaving.

Neil Fox
5 min read
-
 Data Security
Data SecurityMay 21, 2021
How to Analyze Malware with x64dbg
This is the fourth and final article in a series of blog posts that serve as an x64dbg tutorial. In this article, we will be taking all the knowledge we…

Neil Fox
6 min read
-
 Data Security
Data SecurityMay 17, 2021
YARA Rules Guide: Learning this Malware Research Tool
YARA rules are used to classify and identify malware samples by creating descriptions of malware families based on textual or binary patterns.

Neil Fox
7 min read
-
 Data Security
Data SecurityMar 23, 2021
Stack Memory: An Overview (Part 3)
An overview of stack memory, it’s architecture, and how it can be used to reverse-engineer malware using x64dbg.

Neil Fox
9 min read
-
 Data Security PowerShell
Data Security PowerShellMar 22, 2021
How to Use Autoruns to Detect and Remove Malware on Windows
This article acts as a tutorial on how to use Sysinternals Autoruns to detect potentially unwanted software that is installed and running automatically on your device.

Neil Fox
6 min read
-
 Data Security Threat Research
Data Security Threat ResearchMar 17, 2021
How to Unpack Malware with x64dbg
This article is an x64dbg tutorial in which reverse engineering malware methodology will be explained and demonstrated.

Neil Fox
11 min read
-
 Data Security PowerShell
Data Security PowerShellJan 27, 2021
Top 11 Malware Analysis Tools and Their Features
Explore 11 powerful malware analysis tools including traditional and AI-powered options that help security teams detect, dissect, and understand modern threats.

Neil Fox
8 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital