
Michael Buckbee
Michael has worked as a sysadmin and software developer for Silicon Valley startups, the US Navy, and everything in between.
-
 Data Security
Data SecurityApr 01, 2016
PwC Report Shows That Cybercrime Is a Top C-Level Concern
One metric that’s difficult to gauge when it comes to cybercrimes is the economic impact felt by companies. However, PwC took on this challenge and just released the results of...

Michael Buckbee
3 min read
-
 Ransomware
RansomwareMar 28, 2016
Samas, Cerber, Surprise: Three New Ransomware Variants to Have On Your Radar
As of late, the weekly press coverage of ransomware has been building a kind of brand recognition that’s the envy of many legitimate IT vendors. Ransomware’s own success has made...

Michael Buckbee
6 min read
-
 Data Security
Data SecurityMar 17, 2016
There’s Something About Frameworks: A Look at HITRUST’s CSF
Repeat after me: frameworks are not standards. They are instead often used as a guide to navigate through the underlying standards. There are lots of frameworks cropping up in the...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMar 08, 2016
With KeRanger, Mac Users Are No Longer Immune to Ransomware Threats
Cybercriminals who previously targeted Windows operating systems with ransomware have expanded their customer base to include the Mac OS. Known as KeRanger, it’s the first ransomware variant detected that infects...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityMar 03, 2016
Penetration Testing Explained, Part VII: Exfiltration and Conclusions
In this series of posts, I covered ideas to get you started using basic testing software to find security vulnerabilities. There are more advanced tools, such as Metasploit, which lets...

Michael Buckbee
4 min read
-
 Security Bulletins
Security BulletinsFeb 24, 2016
DatAlert Analytics and the Varonis Behavior Research Laboratory
Last November, we introduced Varonis UBA threat models to automatically analyze behavior and detect insider threats throughout the lifecycle of a breach. Our UBA threat models, which are major enhancements...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityFeb 17, 2016
Entrepreneurial RATs: AlienSpy and TaaS (Trojans as a Service)
When I wrote about Remote Access Trojans (RATs), I thought they were like the mousetraps of the hacking world — it’s hard to improve on. RATs let hackers get a...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityFeb 09, 2016
Lessons from the Malware Museum
If you haven’t already seen Mikko Hypponen’s collection of vintage malware at the Internet Archive, take the time for a brief tour. If you’re on a lunch hour, it’s also...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityFeb 05, 2016
New Updates to the CIS Critical Security Controls
If you haven’t already heard, the Top 20 Critical Security Controls has a new name. Last year, after the Center for Internet Security(CIS) integrated with the Council on Cybersecurity, the...

Michael Buckbee
5 min read
-
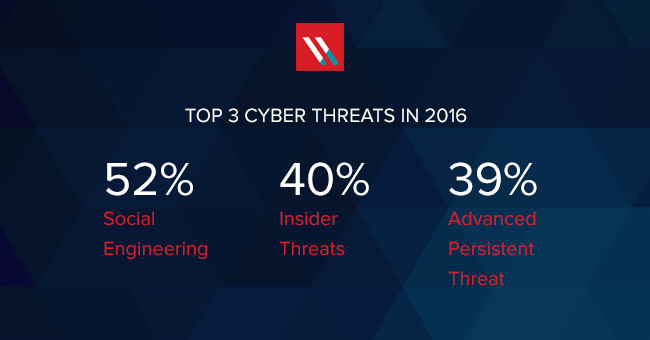 Data Security
Data SecurityJan 21, 2016
Social Engineering Remains a Top Cybersecurity Concern
In 2016, the top cyberthreat for IT pros, at least according to ISACA’s Cybersecurity Snapshot, is social engineering. It has always been a classic exploit amongst the hackerati. But in...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJan 18, 2016
Current Privacy Risks in Genetic Testing
The idea of taking a direct-to-consumer(DTC) genetic test is intriguing. What was once considered an expensive test that could only be performed in a medical environment can now be purchased...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJan 10, 2016
Varonis Seven Part Guide to Penetration Testing
Our sprawling pen-testing series has taken on a life of its own! For your convenience and blog reading pleasure, we’ve assembled all the links to this six seven part series below....

Michael Buckbee
1 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital