
Michael Buckbee
Michael has worked as a sysadmin and software developer for Silicon Valley startups, the US Navy, and everything in between.
-
 PowerShell
PowerShellJun 08, 2017
Disabling PowerShell and Other Malware Nuisances, Part III
One of the advantages of AppLocker over Software Restriction Policies is that it can selectively enable PowerShell for Active Directory groups. I showed how this can be done in the...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityJun 06, 2017
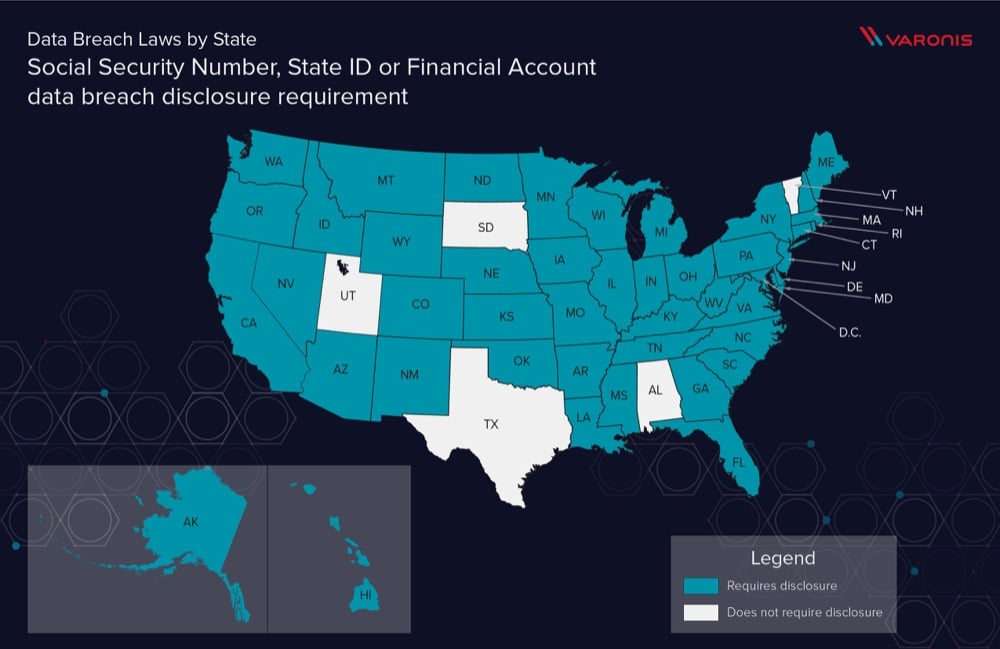
Data Breach Definition by State
State governments are becoming more aware of PII and PHI data breaches, how about your state? See how PII is protected per state with our primer on US State Data Breach Law Definitions.

Michael Buckbee
10 min read
-
 Data Security PowerShell
Data Security PowerShellJun 02, 2017
Disabling PowerShell and Other Malware Nuisances, Part II
Whitelisting apps is nobody’s idea of fun. You need to start with a blank slate, and then carefully add back apps you know to be essential and non-threatening. That’s the...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMay 26, 2017
Disabling PowerShell and Other Malware Nuisances, Part I
Back in more innocent times, circa 2015, we began to hear about hackers going malware-free and “living off the land.” They used whatever garden-variety IT tools were lying around on...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMay 22, 2017
Is a ransomware attack a data breach?
Understanding if ransomware is a data breach is vital to determining what response your IT and Legal department needs to take.

Michael Buckbee
1 min read
-
 PowerShell
PowerShellMay 16, 2017
How to use PowerShell for WannaCry / WannaCrypt cleanup and prevention
Use PowerShell to help test and resolve issues from WannaCry / WannaCrypt variants and other ransomware attacks.

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMay 12, 2017
🚨 Massive Ransomware Outbreak: What You Need To Know
Remember those NSA exploits that got leaked a few months back? A new variant of ransomware using those exploits is spreading quickly across the world – affecting everyone from the...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMay 12, 2017
Planet Ransomware
If you were expecting a quiet Friday in terms of cyberattacks, this ain’t it. There are reports of a massive ransomware attack affecting computers on a global scale: in the...

Michael Buckbee
1 min read
-
 PowerShell
PowerShellMay 10, 2017
Practical PowerShell for IT Security, Part IV: Security Scripting Platform (SSP)
In the previous post in this series, I suggested that it may be possible to unify my separate scripts — one for event handling, the other for classification — into...

Michael Buckbee
10 min read
-
 Security Bulletins
Security BulletinsMay 05, 2017
Introducing the Automation Engine, DatAlert Analytics Rewind, and more
Getting to least privilege can be a nightmare. The first steps – tracking down inconsistent ACLs and remediating global access groups can turn even the most basic file share clean-up...

Michael Buckbee
1 min read
-
 Security Bulletins
Security BulletinsApr 26, 2017
Varonis + Splunk: Epic Threat Detection and Investigations
We’re bringing our powerful DatAlert functionality to Splunk® Enterprise to give you comprehensive visibility into data security with our new Varonis App fo

Michael Buckbee
1 min read
-
 Privacy & Compliance
Privacy & ComplianceApr 20, 2017
Data Security Compliance and DatAdvantage, Part III: Protect and Monitor
At the end of the previous post, we took up the nuts-and-bolts issues of protecting sensitive data in an organization’s file system. One popular approach, least-privileged access model, is often...

Michael Buckbee
5 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital