
Michael Buckbee
Michael has worked as a sysadmin and software developer for Silicon Valley startups, the US Navy, and everything in between.
-
May 05, 2017
Introducing the Automation Engine, DatAlert Analytics Rewind, and more
Getting to least privilege can be a nightmare. The first steps – tracking down inconsistent ACLs and remediating global access groups can turn even the most basic file share clean-up...

Michael Buckbee
1 min read
-

Apr 26, 2017
Varonis + Splunk: Epic Threat Detection and Investigations
We’re bringing our powerful DatAlert functionality to Splunk® Enterprise to give you comprehensive visibility into data security with our new Varonis App fo

Michael Buckbee
1 min read
-
 Privacy & Compliance
Privacy & ComplianceApr 20, 2017
Data Security Compliance and DatAdvantage, Part III: Protect and Monitor
At the end of the previous post, we took up the nuts-and-bolts issues of protecting sensitive data in an organization’s file system. One popular approach, least-privileged access model, is often...

Michael Buckbee
5 min read
-
 Privacy & Compliance
Privacy & ComplianceApr 14, 2017
Data Security Compliance and DatAdvantage, Part II: More on Risk Assessment
I can’t really overstate the importance of risk assessments in data security standards. It’s really at the core of everything you subsequently do in a security program. In this post...

Michael Buckbee
5 min read
-
 Privacy & Compliance
Privacy & ComplianceApr 03, 2017
Data Security Compliance and DatAdvantage, Part I: Essential Reports for Risk Assessment
Over the last few years, I’ve written about many different data security standards, data laws, and regulations. So I feel comfortable in saying there are some similarities in the EU’s...

Michael Buckbee
4 min read
-
 PowerShell
PowerShellMar 22, 2017
Practical PowerShell for IT Security, Part II: File Access Analytics (FAA)
In working on this series, I almost feel that with PowerShell we have technology that somehow time-traveled back from the future. Remember on Star Trek – the original of course...

Michael Buckbee
7 min read
-
 Data Security
Data SecurityMar 08, 2017
Practical PowerShell for IT Security, Part I: File Event Monitoring
Back when I was writing the ultimate penetration testing series to help humankind deal with hackers, I came across some interesting PowerShell cmdlets and techniques. I made the remarkable discovery...

Michael Buckbee
5 min read
-
Feb 13, 2017
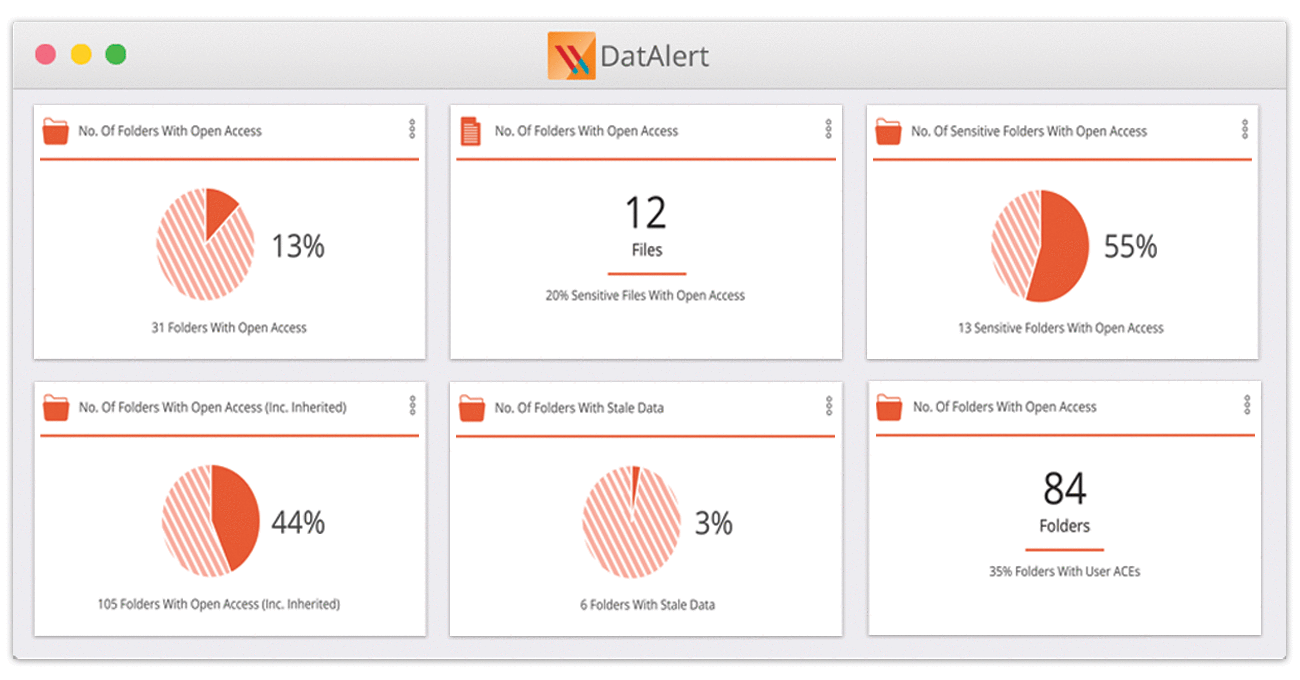
Introducing a new security dashboard, enhanced behavioral analysis, and more
Every day we hear new stories about how our customers are using DatAlert to stop cyberattacks: detecting and disabling ransomware infections, discovering misconfigurations and vulnerabilities, and setting up automatic responses...

Michael Buckbee
1 min read
-
 Active Directory
Active DirectoryFeb 08, 2017
Binge Read Our Pen Testing Active Directory Series
With winter storm Niko now on its extended road trip, it’s not too late, at least here in the East Coast, to make a few snow day plans. Sure you...

Michael Buckbee
1 min read
-
 Active Directory
Active DirectoryJan 27, 2017
Pen Testing Active Directory Environments, Part VI: The Final Case
If you’ve come this far in the series, I think you’ll agree that security pros have to move beyond checking off lists. The mind of the hacker is all about making...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityJan 20, 2017
Connecting Your Data Strategy to Analytics: Eight Questions to Ask
Big data has ushered in a new executive role over the past few years. The chief data officer or CDO now joins the C-level club, tasked with leveraging data science...

Michael Buckbee
3 min read
-
 Active Directory
Active DirectoryJan 17, 2017
Pen Testing Active Directory Environments, Part V: Admins and Graphs
If you’ve survived my last blog post, you know that Active Directory group structures can be used as powerful weapons by hackers. Our job as pen testers is to borrow...

Michael Buckbee
6 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital