
Jason Hill
Jason is a Security Researcher within the Varonis Research Team and has a penchant for all-things threat intelligence. Equally happy analyzing nefarious files or investigating badness, Jason is driven by the desire to make the cyber world a safer place.
-
 Threat Research
Threat ResearchJul 02, 2024
OpenSSH 'RegreSSHion' RCE Vulnerability
A critical vulnerability in OpenSSH's server, dubbed 'regreSSHion,' raises the risk of remote code execution with root privileges.

Jason Hill
4 min read
-
 Threat Research
Threat ResearchMar 20, 2024
Increased Threat Activity Targeting Ivanti Vulnerabilities
A recent surge in activity targeting Ivanti Connect Secure (ICS) involves chaining two vulnerabilities that give threat actors the ability to execute arbitrary commands remotely.

Jason Hill
2 min read
-
 Threat Research
Threat ResearchJul 18, 2023
Taking Microsoft Office by "Storm"
The “Storm-0978” ransomware group is actively exploiting an unpatched Microsoft Office and Windows HTML remote code execution vulnerability.

Jason Hill
3 min read
-
 Threat Research
Threat ResearchFeb 20, 2023
HardBit 2.0 Ransomware
HardBit is a ransomware threat that targets organizations to extort cryptocurrency payments for the decryption of their data. Seemingly improving upon their initial release, HardBit version 2.0 was introduced toward the end of November 2022, with samples seen throughout the end of 2022 and into 2023.

Jason Hill
8 min read
-
 Threat Research
Threat ResearchFeb 07, 2023
VMware ESXi in the Line of Ransomware Fire
Servers running the popular virtualization hypervisor VMware ESXi have come under attack from at least one ransomware group over the past week, likely following scanning activity to identify hosts with Open Service Location Protocol (OpenSLP) vulnerabilities.

Jason Hill
10 min read
-
 Threat Research
Threat ResearchAug 22, 2022
Anatomy of a SolidBit Ransomware Attack
Solidbit is a ransomware variant derived from Yashma and containing elements of LockBit. Discover how Solidbit's capabilities, execution, what file types it targets, and how to tell if you're been infected.

Jason Hill
6 min read
-
 Threat Research
Threat ResearchJun 16, 2022
Rogue Shortcuts: LNK'ing to Badness
Learn how threat actors continue to manipulate Windows shortcut files (LNKs) as an exploit technique.

Jason Hill
5 min read
-
 Threat Research
Threat ResearchMar 04, 2022
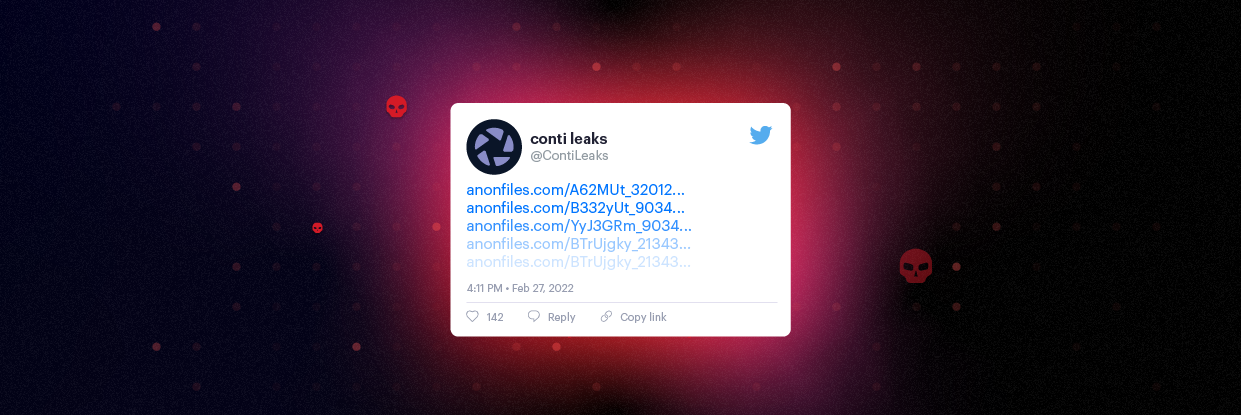
ContiLeaks: Ransomware Gang Suffers Data Breach
Conti, a prolific ransomware group, has suffered a leak of both internal chat transcripts and source code being shared by a reported Ukrainian member

Jason Hill
6 min read
-
 Threat Research
Threat ResearchJan 26, 2022
BlackCat Ransomware (ALPHV)
Varonis has observed the ALPHV (BlackCat) ransomware, actively recruiting new affiliates and targeting organizations across multiple sectors worldwide.

Jason Hill
9 min read
-
 Threat Research
Threat ResearchOct 19, 2021
Good for Evil: DeepBlueMagic Ransomware Group Abuses Legit Encryption Tools
A group known as "DeepBlueMagic" is suspected of launching a ransomware attack against Hillel Yaffe Medical Center in Israel, violating a loose "code of conduct" that many ransomware groups operate...

Jason Hill
7 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital