
Eric Saraga
Eric Saraga joined the company in 2016 and is a Varonis Threat Labs Security Research Team leader. He enjoys researching Windows and cloud environments, finding vulnerabilities, and catching attackers.
-
 Threat Research
Threat ResearchApr 09, 2024
Sidestepping SharePoint Security: Two New Techniques to Evade Exfiltration Detection
Varonis Threat Labs discovered two techniques in SharePoint that allow users to circumvent audit logs and avoid triggering download events while exfiltrating files.

Eric Saraga
6 min read
-
 Threat Research
Threat ResearchMar 11, 2022
Is this SID taken? Varonis Threat Labs Discovers Synthetic SID Injection Attack
A technique where threat actors with existing high privileges can inject synthetic SIDs into an ACL creating backdoors and hidden permission grants.

Eric Saraga
3 min read
-
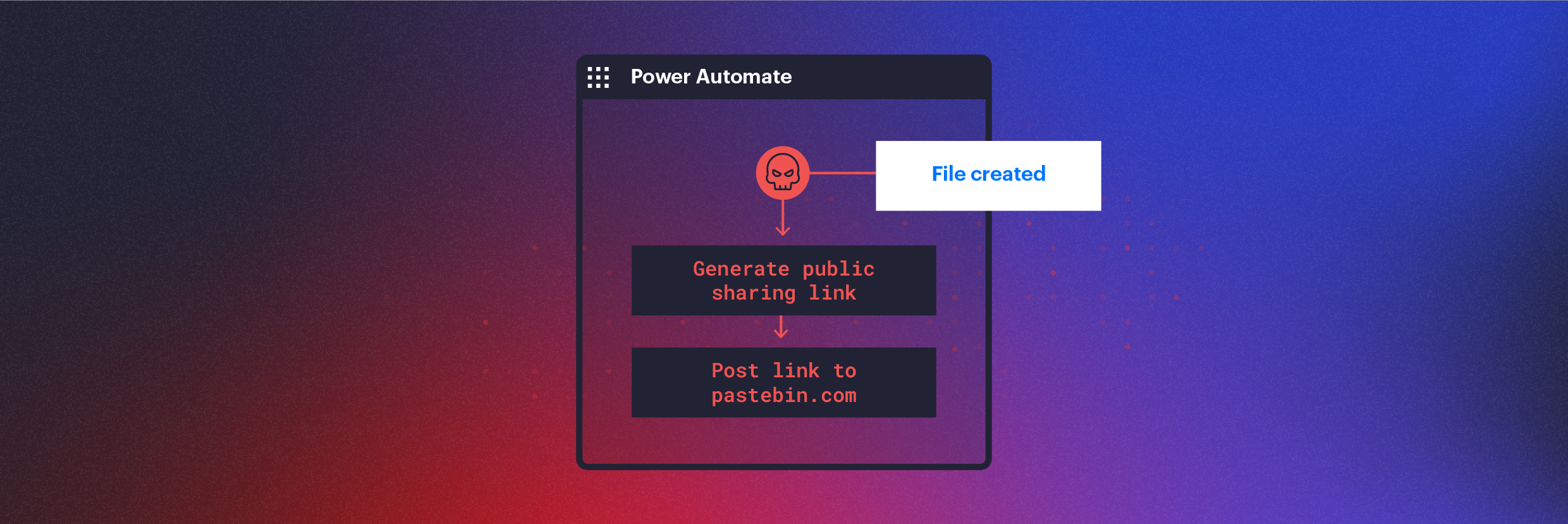 Threat Research
Threat ResearchFeb 02, 2022
Using Power Automate for Covert Data Exfiltration in Microsoft 365
How threat actors can use Microsoft Power Automate to automate data exfiltration, C2 communication, lateral movement, and evade DLP solutions.

Eric Saraga
5 min read
-
 Data Security
Data SecurityAug 20, 2020
Using Malicious Azure Apps to Infiltrate a Microsoft 365 Tenant
Phishing remains one of the most successful ways to infiltrate an organization. We’ve seen a massive amount of malware infections stemming from users opening infected attachments or clicking links that...

Eric Saraga
5 min read
-
 Data Security Threat Research
Data Security Threat ResearchApr 22, 2020
Azure Skeleton Key: Exploiting Pass-Through Auth to Steal Credentials
We created a proof-of-concept that manipulates the Azure authentication function to give us a ‘skeleton key’ password that will work for all users, and dump all real clear-text usernames and passwords into a file.

Eric Saraga
6 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital