Think about your most recent security awareness training concerning phishing attacks. It likely included guidelines about avoiding clicking on suspicious links and exercises to identify subtle character differences, such as distinguishing between the letter “O” and a zero.
Unfortunately, the time when even the most novice technology user could easily recognize a phishing email has ended.
In the last few years, attackers have become more sophisticated and creative. Typo mistakes and grammar issues are no longer a concern for non-English-speaking threat actors, as the rapid evolution of AI has significantly contributed to the quality of these attacks.
Recently, the Varonis Managed Data Detection and Response (MDDR) forensics team investigated a clever phishing campaign in which a malicious email enabled a threat actor to access the organization.
This blog post will reveal the tactics the threat actor used to avoid detection and share the IoCs discovered during our investigation.
Technical overview
A U.K.-based insurance customer faced a unique phishing attack. It began when a deletion rule created from a U.S. IP address was found in an executive manager’s mailbox. This rule, named “a,” permanently deleted emails containing a specific keyword in the email address.
After the customer was alerted to the attack, the Varonis MDDR team identified the phishing email titled “ML Payment #05323” and its sender. We mapped out all email recipients, those who responded, those who reported it, and other communications with the threat actor’s domain. This comprehensive spreadsheet was crucial for incident containment.
Initially, our only indicators of compromise were the recipient’s email address and the source IP of the deletion rule creation event, which turned out to be a general Microsoft IP and, therefore, not very useful in that case.
However, the investigation took an interesting turn when we discovered that the phishing email appeared to come from a trusted sender: the CEO of a major international shipping company, who had previously communicated with our customer’s employees. The threat actor probably compromised the CEO’s email account, using it to damage more organizations.
The specific keyword in the deletion rule was part of the sender’s domain. It was designed to erase all emails to or from this domain, leaving no trace. The next step was to analyze the original EML file to understand the phishing methodology.
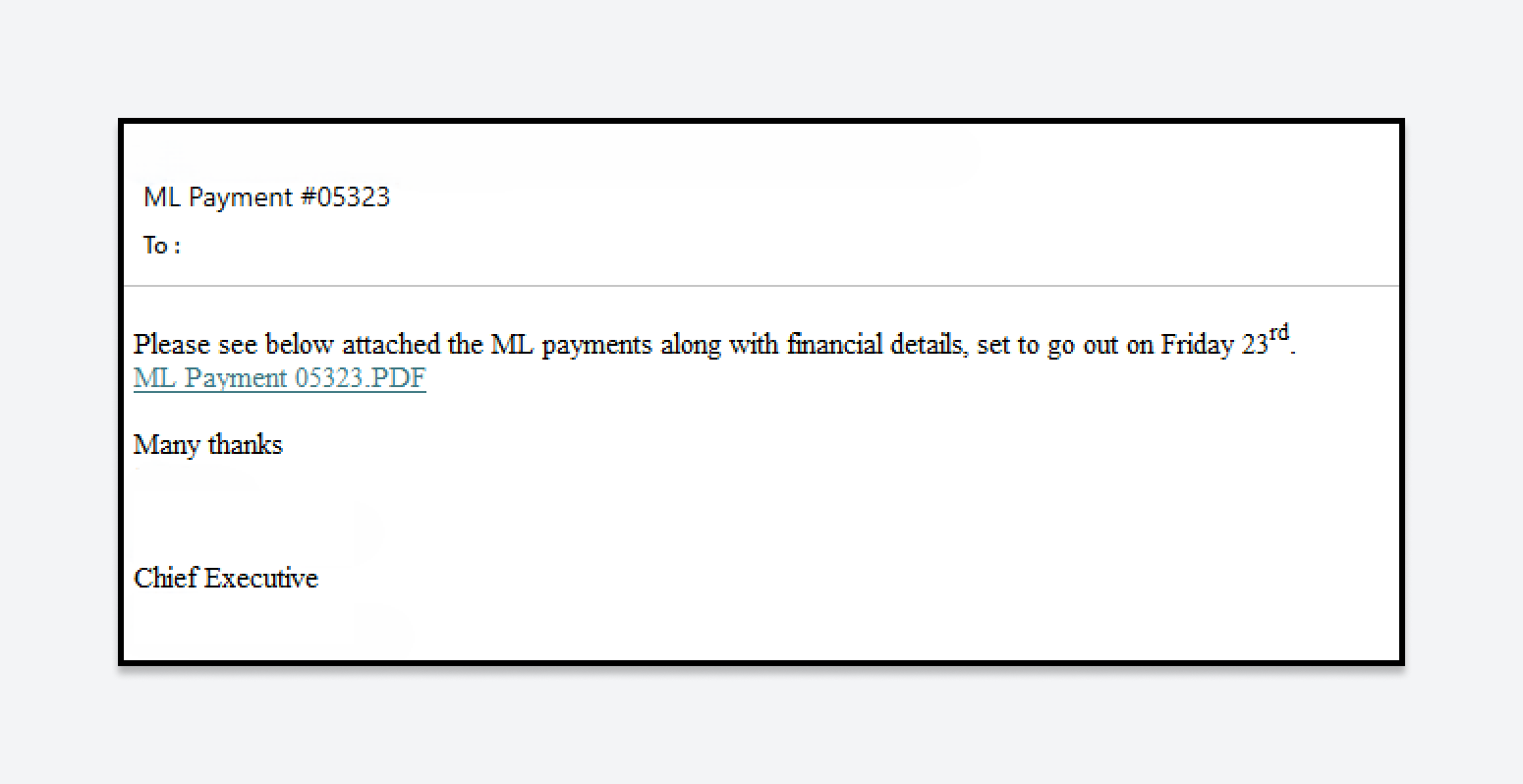
The original phishing email was sent to 26 recipients in the organization. Instead of attaching a PDF file, the email included a link to a PDF hosted on an AWS server.
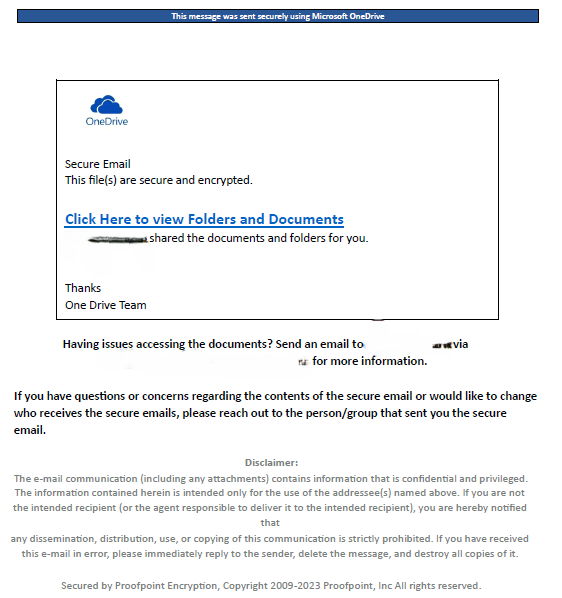
The PDF appeared to be an official OneDrive message, indicating that the sender had shared a file. While a cybersecurity professional might identify the email as a phishing attempt, the high-quality message could easily deceive the average user.
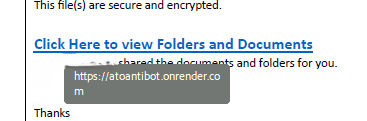
Interestingly, the PDF link contained the phrase “atoantibot.” ATO stands for account takeover. At first glance, the link appeared to protect against ATO attacks, but the phishing attempt was ultimately the exact opposite. This bit of “hacker humor” will be revisited later in the article.
To develop part of the attack, the threat actor used the public platform Render, a unified cloud platform that allows developers to build, deploy, and scale applications and websites easily. By leveraging a legitimate platform, the attacker ensured their malicious activities blended in seamlessly, making it difficult for email security systems to detect the threat.
After clicking to “view the shared document,” the user was redirected to “login.siffinance[.]com”, a fake Microsoft authentication page. At this point, when the victim entered his credentials, the attacker achieved his goal. The user was then redirected to the official Microsoft Office site, making the incident seem like a glitch.
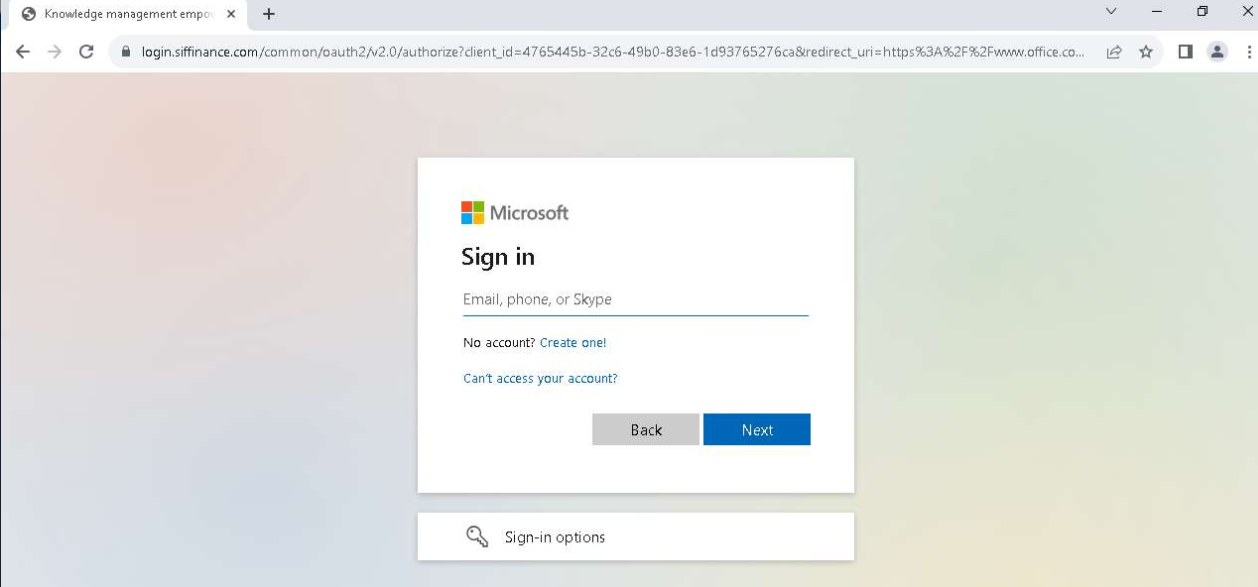
Circling back to the “hacker humor” mentioned above, the attacker has disabled (or deactivated) the malicious domain, but if you try to access it today, it redirects to a popular internet prank known as Rickrolling.
After entering credentials on the phishing page, the victim inexplicably responded to the attacker’s email. However, because the customer could not retrieve the sent email, the content of the message is a mystery. Two minutes later, a successful login from a U.S. IP address (138.199.52[.]3) was detected, despite the victim being in the U.K. This “impossible travel” confirmed the attacker’s access.
Fortunately, our customer’s security team acted swiftly, disabling the account, ending the session, and resetting the user’s credentials within 30 minutes. The only action the attacker successfully achieved was creating a deletion rule.
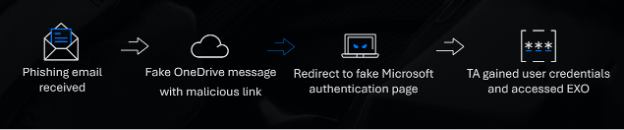
Our investigation revealed that this incident was part of a broader phishing campaign targeting multiple companies. The attacker employed several sophisticated tactics that made detection and investigation challenging:
- Covering their tracks: After gaining access to the victim’s M365 environment, the first action was to create a deletion rule.
- Using a trusted sender address: The attacker used a familiar email address, reducing suspicion among employees.
- Leveraging legitimate platforms: AWS hosted the malicious PDF, and Render was used to build a part of the attack website. These platforms helped the attacker evade email security software.
- The Russian nesting dolls method: Similar to nesting dolls, the attacker embedded multiple links within one another, creating a complex chain that obscured the final phishing site. Each link led to another legitimate-looking page, using credible platforms to bypass email security filters. This made the phishing email appear harmless and difficult to detect. By the time the user reached the fake authentication page, they were weary from navigating multiple sites, making them less attentive and more likely to fall for the scam.
Recommendations
User security awareness
As is often the case in cybersecurity, the process begins and ends with users' security awareness. While it can be challenging for the average user to recognize sophisticated phishing emails, there are several best practices you can educate your users on to help them avoid falling into these traps:
- Email habits: Encourage users to open messages or shared files directly from the relevant platform instead of clicking on email links.
- Link verification: Hover over email links to check the URL. Ensure it logically matches the email content.
- Credential safety: Verify the URL of the authentication page before entering credentials.
- Phishing recognition: Educate users on identifying phishing emails and understanding the associated risks.
Technical measures
Below are a few technical steps that will help you protect against phishing and account take-over attacks:
- Password policy: Enforce complex passwords and require changes every 90 days.
- Multifactor authentication (MFA): Implement MFA for all users.
- Email security: Adopt a robust email security solution.
- Reporting mechanism: Provide an easy way for users to report suspicious emails.
- External email warnings: Add default warnings for emails received from external sources.
IoCs
- 138.199.52[.]3
- siffinance[.]com
- login.siffinance[.]com
- www.siffinance[.]com
- ywnjb.siffinance[.]com
- atoantibot.onrender[.]com
- file365-cloud.s3.eu-west-2.amazonaws[.]com
How Varonis can help
Varonis monitors real-time email and browsing activities and user and data activities, providing a comprehensive tool for cyber forensics investigations. This lets you quickly determine the impact and potential risks of a phishing campaign targeting your organization.
The Varonis MDDR team offers 24/7/365 data security expertise and incident response, ensuring continuous support for virtually any security concern.
Want to see Varonis in action? Schedule a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.