Ransomware’s Early Days
The first documented and purported example of ransomware was the 1989 AIDS Trojan, also known as PS Cyborg1. Harvard-trained evolutionary biologist Joseph L. Popp sent 20,000 infected diskettes labeled “AIDS Information – Introductory Diskettes” to attendees of the World Health Organization’s international AIDS conference.
But after 90 reboots, the Trojan hid directories and encrypted the names of the files on the customer’s computer. To regain access, the user would have to send $189 to PC Cyborg Corp. at a post office box in Panama. Dr. Popp was eventually caught but never tried for his scheme as he was declared unfit to stand trial. His attorney said he began wearing a cardboard box on his head to protect himself from radiation2.
Get a Free Data Risk Assessment
Fast Forward to the Internet Age
With the Internet making it easier to carry out Popp’s ransom idea, cyber criminals began to realize that they could monetize ransomware on a far wider scale.
In 2006, criminal organizations began using more effective asymmetric RSA encryption.
- The Archiveus Trojan3 encrypted everything in the My Documents directory and required victims to purchase items from an online pharmacy to receive the 30-digit password.
- The GPcode4, an encryption Trojan, which initially spread via an email attachment purporting to be a job application, used a 660-bit RSA public key. Two years later, a variant (GPcode.AK) used a 1024-bit RSA key.
The New Wave
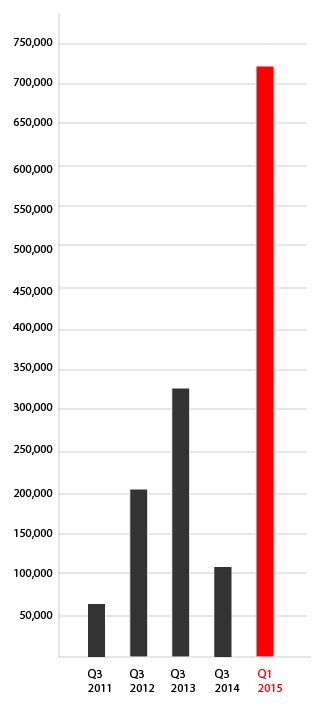
Starting 2011, ransomware moved into big time. About 60,000 new ransomware was detected in Q3 2011, and more than doubled in Q3 2012, to over 200,000.5 What’s most astounding is that from Q3 2014 to Q1 2015, ransomware more than quadrupled.
With no signs of slowing down, there are now many, many ransomware variants. Here’s a brief rundown of the ones you should know:
CryptoLocker – first versions appear to have been posted September 20136
- Usually enters the company by email.
- If a user clicks on the executable, it starts immediately scanning network drives, renames all the files & folders and encrypts them.
Locker – first copycat software emerged in December 20137
- $150 to get the key, with money being sent to a Perfect Money or QIWI Visa Virtual Card number.
CryptoLocker 2.0 – a new and improved version of CryptoLocker was found in December 20138
- CryptoLocker 2.0 was written using C# while the original was in C++.
- Tor and Bitcoin used for anonymity and 2048-bit encryption.
- The latest variant is not detected by anti-virus or firewall.
CryptorBit – a new ransomware discovered in December 20139
- CryptorBit corrupts the first 1024 bytes of any data file it finds.
- Can bypass Group Policy settings put in place to defend against this type of ransomware infection.
- Social engineering used to get end users to install the ransomware using such devices as a fake flash update or a rogue antivirus product.
- Tor and Bitcoin again used for a ransom payment.
- Also installs crypto-coin mining software that uses the victim’s computer to mine digital currency.
CTB-Locker (Curve-Tor-Bitcoin Locker) – discovered midsummer 201410
- First infections were mainly in Russia. The developers were thought to be from an eastern European country.
SynoLocker – appeared in August 201411
- This one attacked Synology NAS devices. SynoLocker encrypted files one by one.
- Payment was in Bitcoins and again Tor was used for anonymity.
CryptoWall – rebranded from CryptoDefense in April 201412
- Exploited a Java vulnerability.
- Malicious advertisements on domains belonging to Disney, Facebook, The Guardian newspaper and many others led people to sites that were CryptoWall infected and encrypted their drives.
- According to an August 27 report from Dell SecureWorks Counter Threat Unit (CTU): “CTU researchers consider CryptoWall to be the largest and most destructive ransomware threat on the Internet as of this publication, and they expect this threat to continue growing.”
- More than 600,000 systems were infected between mid-March and August 24, with 5.25 billion files being encrypted. 1,683 victims (0.27%) paid a total $1,101,900 in ransom. Nearly 2/3 paid $500, but the amounts ranged from $200 to $10,000.13
Cryptoblocker – new ransomware variant emerged in July 201414
- only encrypt files <100MB and will skip anything in Windows or Program Files.15
- It uses AES rather than RSA encryption.
OphionLocker – surprise! Another ransomware released during the holidays, December 201416
- ECC (elliptic curve cryptography) public-key encryption.
- 3 days to pay the ransom or the private key will be deleted.
Pclock – greets the New Year, January 2015 by miming CryptoLocker17
- Files in a user’s profile are encrypted.
- Volume shadow copies are deleted and disabled.
- 72-hour countdown timer to pay 1 bitcoin in ransom.
CryptoWall 2.0 – ransomware goes on steroids in January 201518
- Delivered via email attachments, malicious pdf files and various exploit kits.
- Encrypts the user’s data, until a ransom is paid for the decryption key.
- Uses TOR to obfuscate the C&C (Command & Control) channel.
- Incorporates anti-vm and anti-emulation checks to hamper identification via sandboxes.
- Has the ability to run 64-bit code directly from its 32-bit dropper. It can switch the processor execution context from 32 bit to 64 bit.
TeslaCrypt – a new CryptoWall variant surfaced in February 201519
- Targets popular video game files such as Call of Duty, MineCraft, World of Warcraft, and Steam.
VaultCrypt – pretended to be customer support in February 201520
- First circulated in Russia.
- Uses Windows batch files and open source GnuPG privacy software for file encryption.
CryptoWall 3.0 – a new version appeared March 201521
- I2P network communication.
- Uses exploit kits to gain privilege escalation on the system.
- Disables many security features on a target system.
CryptoWall 4.0 – 6 months later, in September 2015, a new variant is on the loose22
- The most important change from CryptoWall 3.0 to 4.0 is that it re-encrypts filenames of the encrypted files, making it more difficult to decipher which files need to be recovered.
LowLevel04 – this file-encrypting ransomware greeted us in October 201523
- Also known as the Onion Trojan-Ransom
- Spreads via brute force attacks on machines with Remote Desktop or Terminal Services
- Encrypts files using AES encryption but the encryption key itself is RSA encrypted
And finally, a game changer known as Chimera – November 201524
- The hackers will publish the encrypted files on the Internet if the victim doesn’t pay!
Is public disclosure the next phase of ransomware? I’ll discuss Chimera and its implications in my next post.
If you want more details on how to combat this very real problem, we wrote an excellent how-to on detecting and cleaning CryptoLocker infections. It was based on working with our customers to identify files that had been encrypted by CryptoLocker with DatAdvantage. We also created step-by-step instructions tosetup DatAlert to detect CryptoLocker.
Feel free to contact us if you have questions, or if you’d like to set up a free consultation.
1 http://virus.wikia.com/wiki/AIDS_trojan_disk
2 https://medium.com/un-hackable/the-bizarre-pre-internet-history-of-ransomware-bb480a652b4b
3 https://www.knowbe4.com/archiveus-trojan
4 https://www.knowbe4.com/gpcode
5 http://www.mcafee.com/us/resources/reports/rp-quarterly-threat-q4-2012.pdf
6 http://www.bbc.com/news/technology-25506020
7 https://community.webroot.com/t5/Security-Industry-News/Cryptolocker-copycat-ransomware-emerges-but-an-antidote-is/td-p/73029
8 http://news.softpedia.com/news/CryptoLocker-2-0-Appears-to-Be-the-Work-of-Copycats-411191.shtml
9 http://www.bleepingcomputer.com/forums/t/517689/howdecrypt-or-cryptorbit-encrypting-ransomware-500-usd-ransom-topic/
10 https://www.knowbe4.com/curve-tor-bitcoin-locker
11 https://www.knowbe4.com/synolocker
12 http://www.secureworks.com/cyber-threat-intelligence/threats/cryptowall-ransomware/
13 https://www.knowbe4.com/cryptowall
14 http://blog.trendmicro.com/trendlabs-security-intelligence/new-crypto-ransomware-emerge-in-the-wild/
15 http://blog.trendmicro.com/trendlabs-security-intelligence/new-crypto-ransomware-emerge-in-the-wild/
16 http://www.bleepingcomputer.com/forums/t/559343/ophionlocker-ransomware-encrypts-your-files-with-elliptical-curve-cryptography/
17 http://www.bleepingcomputer.com/forums/t/561970/new-pclock-cryptolocker-ransomware-discovered/
18 http://arstechnica.com/information-technology/2015/01/inside-cryptowall-2-0-ransomware-professional-edition/
19 http://malwaretips.com/blogs/remove-restore_files-txt-and-abc-virus/
20 http://blog.emsisoft.com/2015/03/29/vaultcrypt-ransomware-offers-fake-customer-support/
21 https://malwaretips.com/blogs/remove-cryptowall-3-0-virus/
23 http://www.bleepingcomputer.com/news/security/help-recover-files-txt-ransomware-installed-by-targeted-terminal-services-attacks/
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.